Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Descrição
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

An Overview of MS-RPC and Its Security Mechanisms
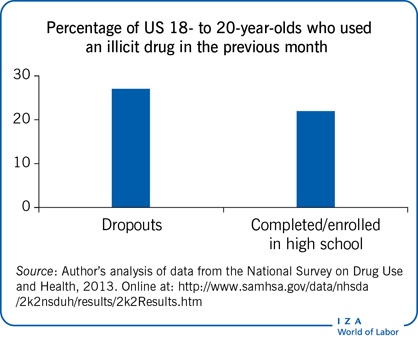
IZA World of Labor - Does substance use affect academic performance?

Exploiting OGNL Injection in Apache Struts

RESTful API: How to Manage Rate Limit Abuse

Changing Spring Boot Env Properties at Runtime

CVE-2021-31956 Exploiting the Windows Kernel (NTFS with WNF
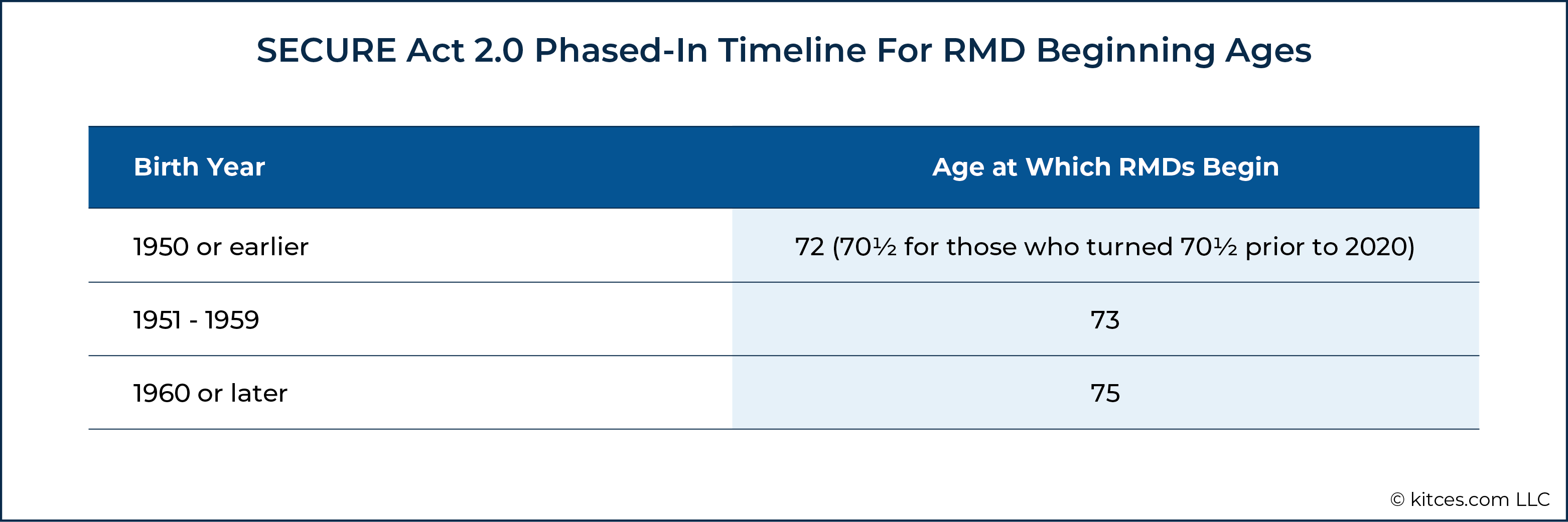
Secure Act 2.0: Detailed Breakdown Of Key Tax Opportunities

Michigan LPC Legal and Ethical Issues in Clinical Supervision

Defining 'Abusive Conduct' Under California Law: A
Blindside: A New Technique for EDR Evasion with Hardware
Mitigating Abuse of Android Application Permissions and Special

Epigenetics - Wikipedia
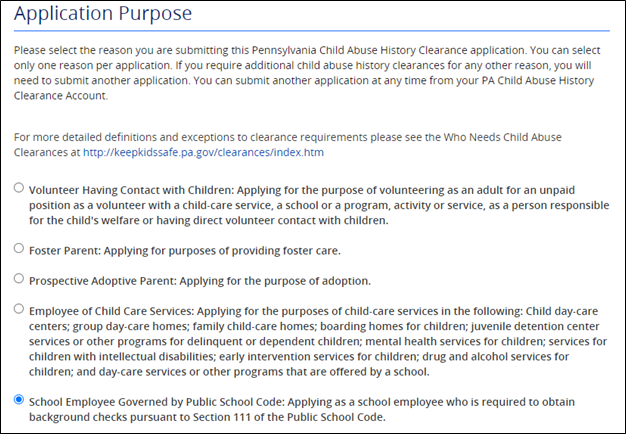
Instructions for Obtaining a Pennsylvania Child Abuse History

WordPress 5.0.0 Remote Code Execution
de
por adulto (o preço varia de acordo com o tamanho do grupo)