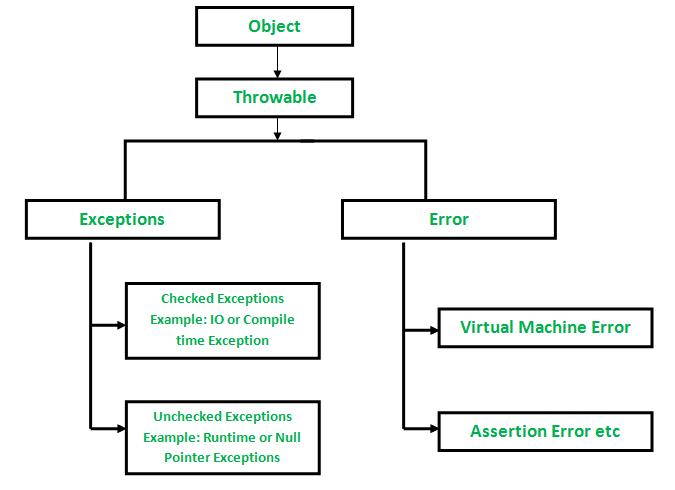
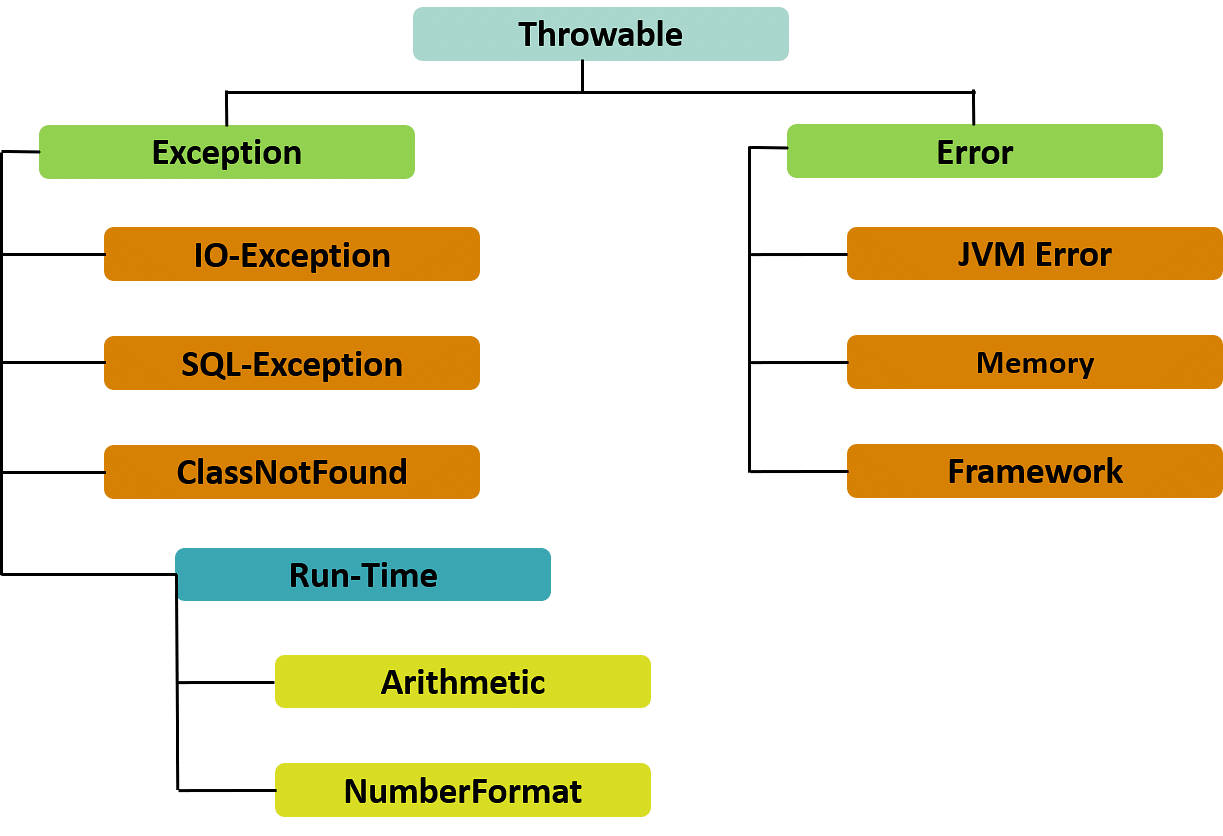
Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Descrição
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

What is a Buffer Overflow, Attack Types and Prevention Methods
For a Better Life: Migrant Worker Abuse in Bahrain and the Government Reform Agenda
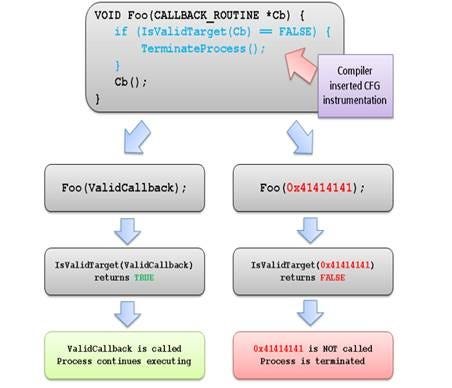
Exploitation Protections From Old To Bleeding Edge pt 1, by Edward Amaral Toledano, stolabs
10 Common Web Security Vulnerabilities

XSS Filter Evasion

Epigenetics - Wikipedia
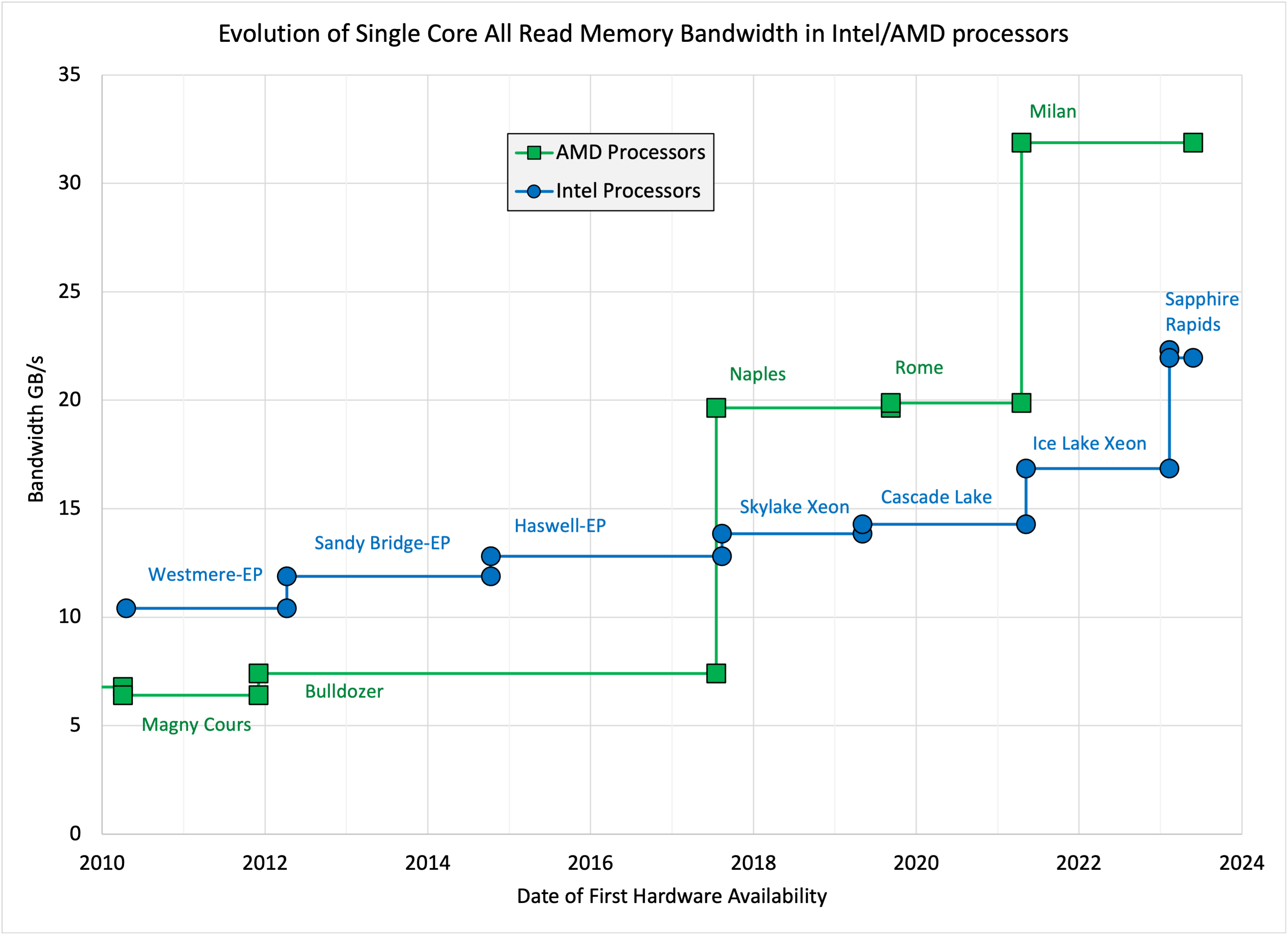
John McCalpin's blog » STREAM benchmark
We believe urinary health should be proactive, but life happens. That’s why we created the UTI Emergency Kit. , This 3-in-1 bundle contains everything

UTI Emergency Kit

What is Remote Code Execution (RCE) Vulnerability❓

Loophole Abuse - TV Tropes

Google finds 18 zero-day vulnerabilities in Samsung Exynos chipsets

Cybersecurity and digital trade: Getting it right

Routing and storage overview, Cloud Logging
de
por adulto (o preço varia de acordo com o tamanho do grupo)