Harnessing the Power of LOLBins and Macros: A Unique Approach to
Por um escritor misterioso
Descrição
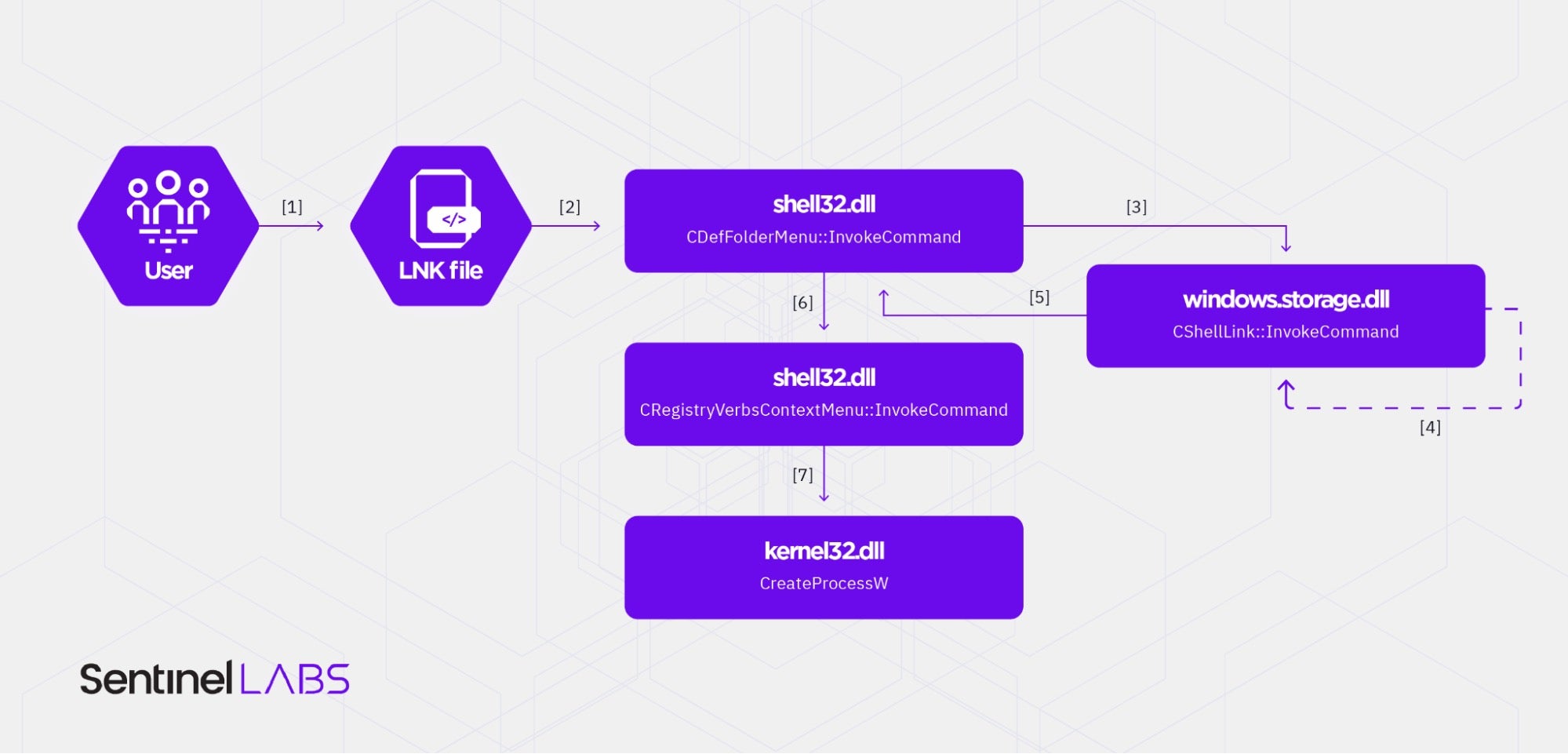
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and
LOLBins: how native tools are used to make threats stealthier
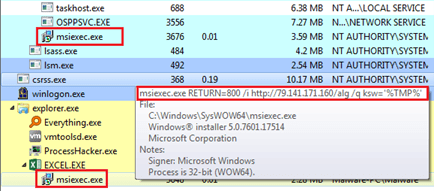
Security 101: What are LOLBins and How Can They be Used
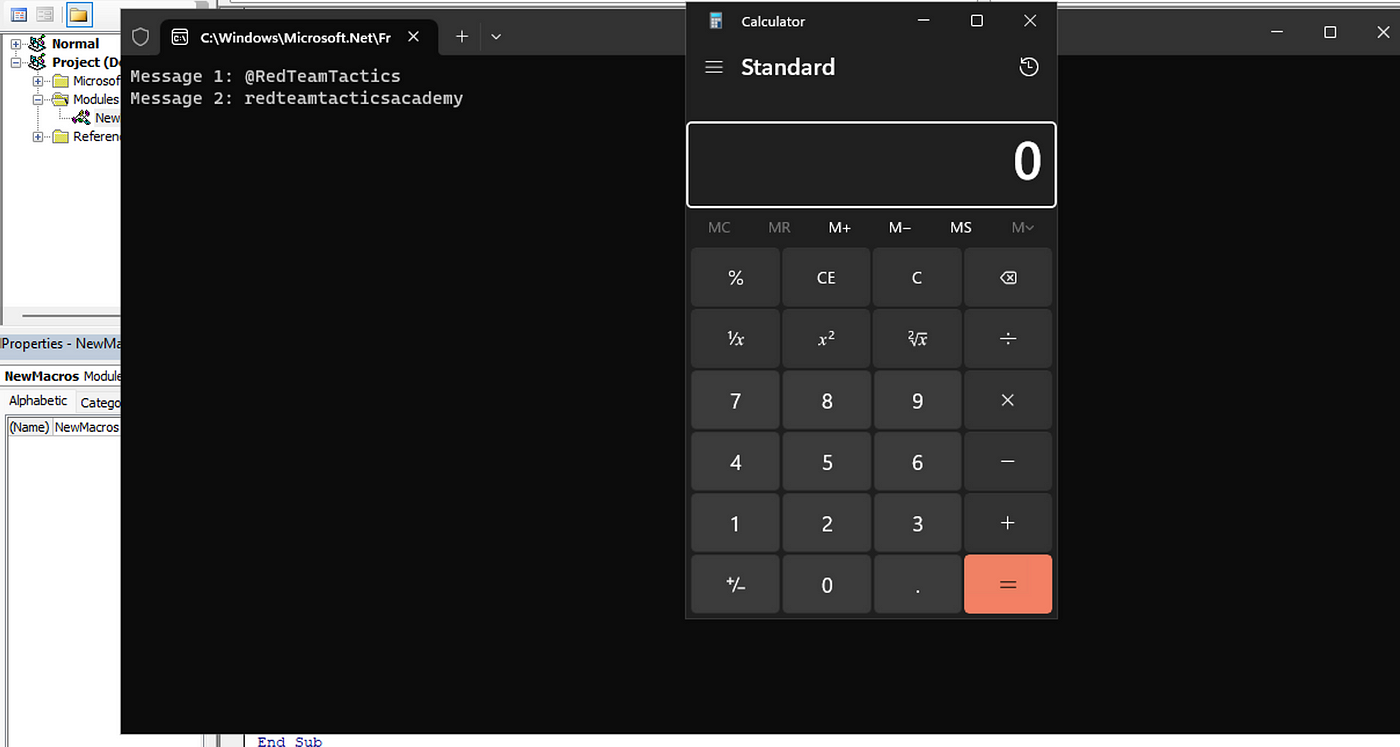
Harnessing the Power of LOLBins and Macros: A Unique Approach to

Swedish Windows Security User Group » Eric Avena

Security and Networking Blog

Data Center Vulnerability Exposed by Multiple Issues in CyberPower

Hackers Attack 1.5 million WordPress Sites by Leveraging a Cookie

EvilProxy Exploits indeed.coms Open Redirect for Microsoft 365
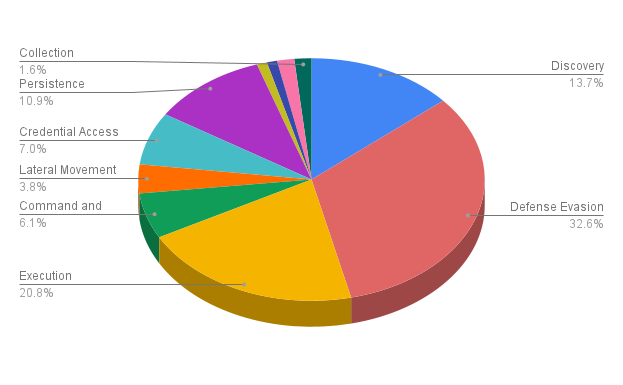
LOLBins Are No Laughing Matter: How Attackers Operate Quietly

Threat Group Winter Vivern Exploiting a Zimbra Vulnerability to

Researchers Found Threat Actors Abusing Google Ads to Spread Malware

Security and Networking Blog

Swedish Windows Security User Group
de
por adulto (o preço varia de acordo com o tamanho do grupo)






/cloudfront-eu-central-1.images.arcpublishing.com/prisa/RTXRGJTUJJDINGHHZRJX2KVKPQ.jpg)