Malware analysis Suspicious activity
Por um escritor misterioso
Descrição
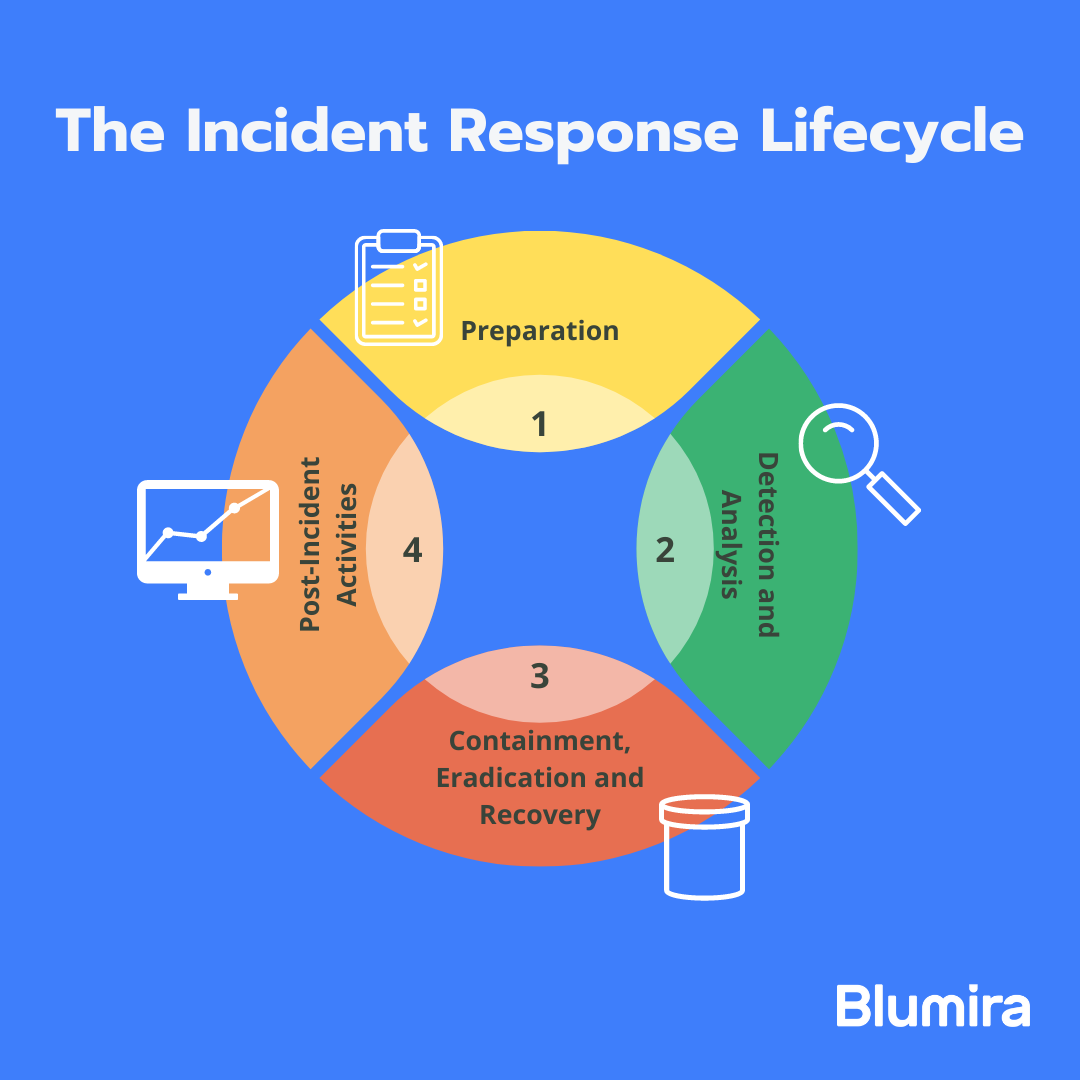
Building Effective Incident Response Procedures

Security Orchestration Use Case: Automating Malware Analysis

Malware Analysis: Steps & Examples - CrowdStrike

How to Analyze Malware Infections?

Malware Analysis Framework v1.0

Using Python for Malware Analysis — A Beginners Guide

Malware Analysis Benefits Incident Response

How to Detect New Threats via Suspicious Activities
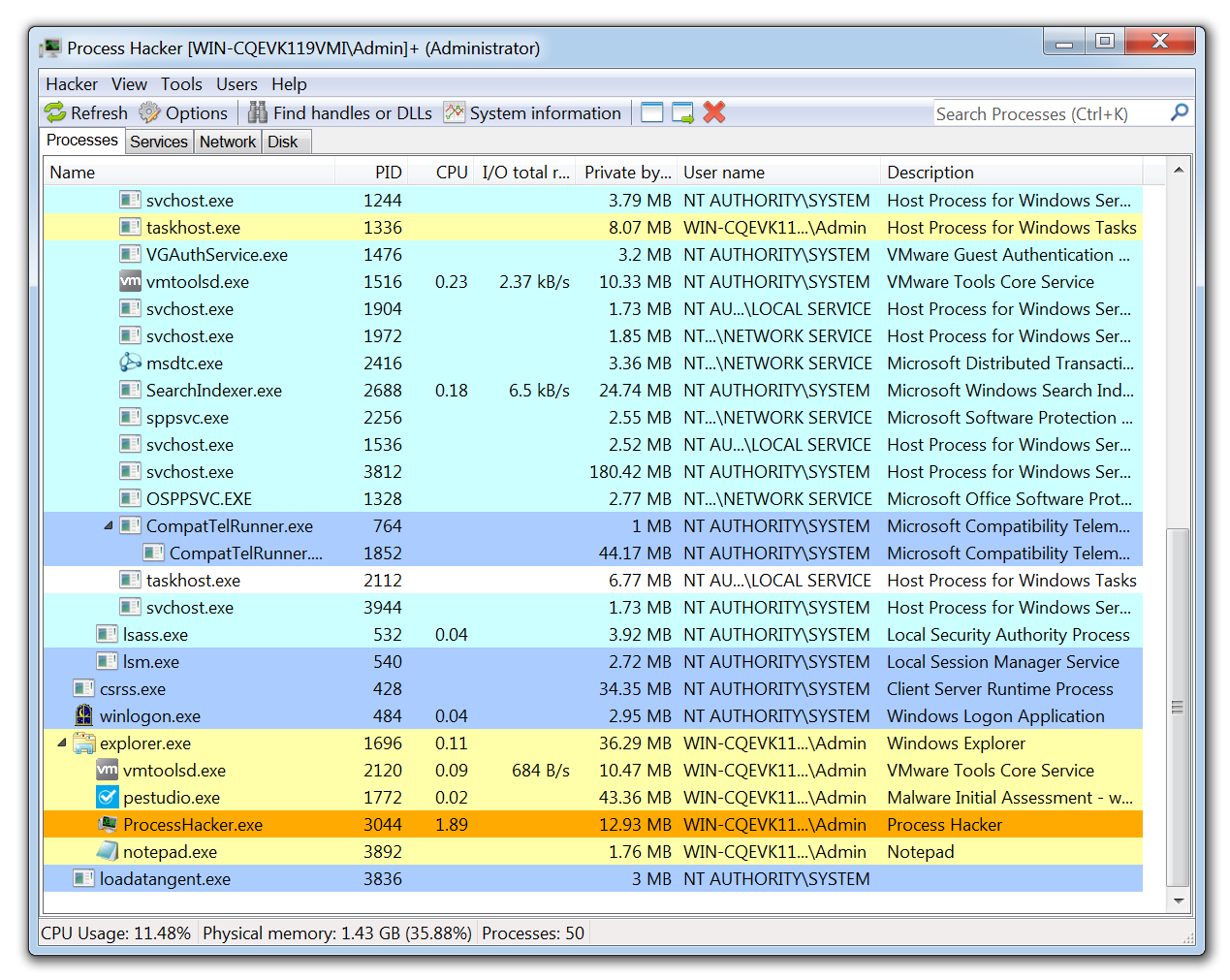
11 Best Malware Analysis Tools and Their Features

How to Detect New Threats via Suspicious Activities
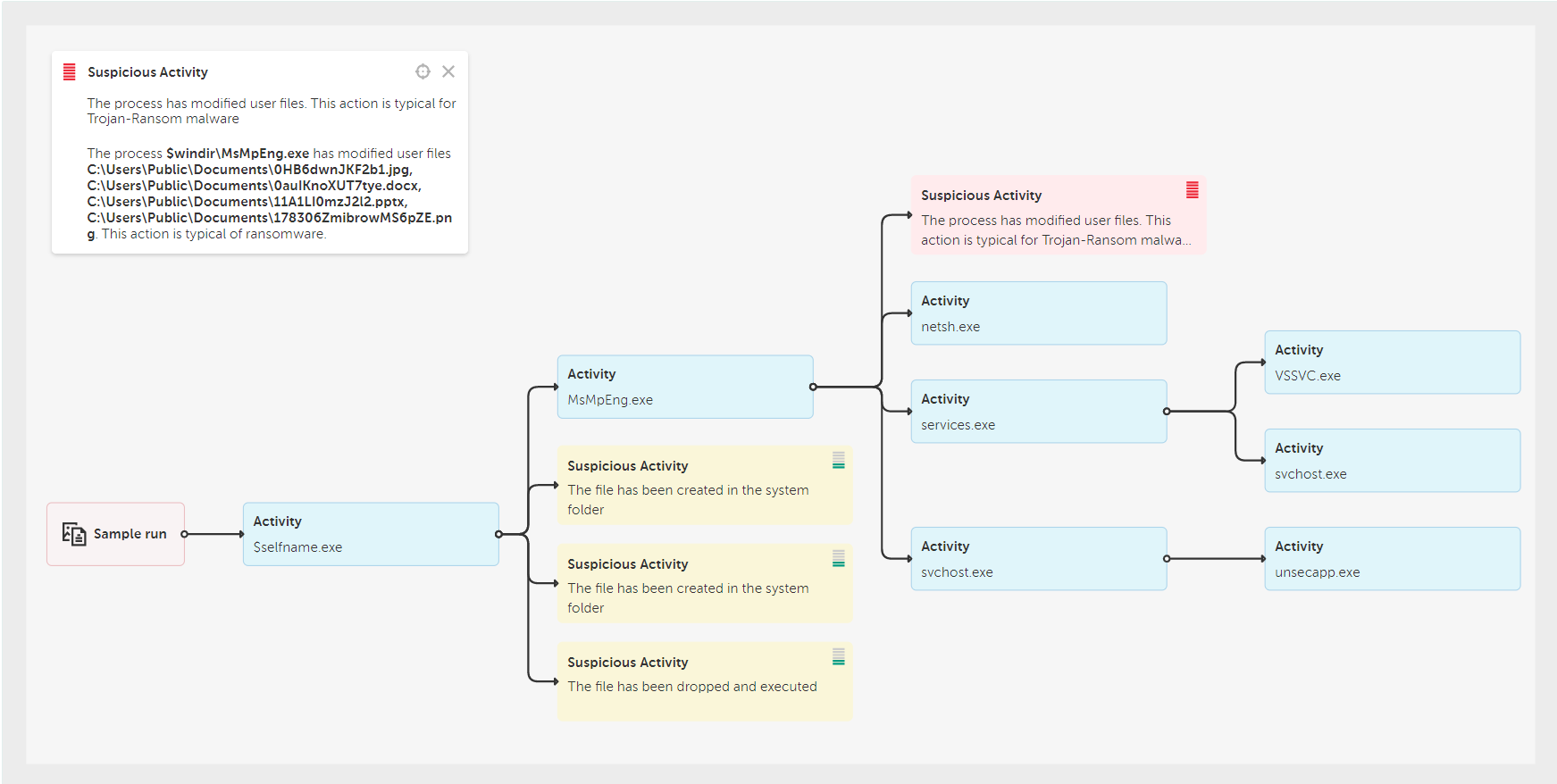
REvil ransomware attack against MSPs and its clients around the
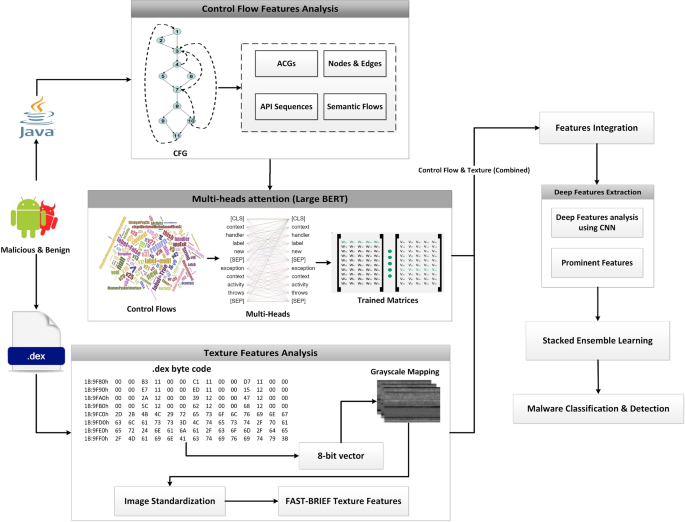
A malware detection system using a hybrid approach of multi-heads

Malware Analysis Benefits Incident Response
How to Get Free Malware Samples and Reports - 's
de
por adulto (o preço varia de acordo com o tamanho do grupo)





