Open Files: How Do You Exploit them?
Por um escritor misterioso
Descrição
It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…

Microsoft patches document exploit vulnerability
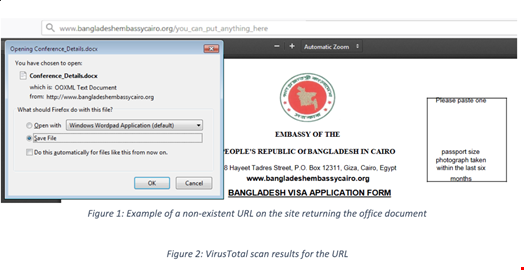
Hackers Exploit Bangladesh Embassy in Cairo Site - Infosecurity Magazine
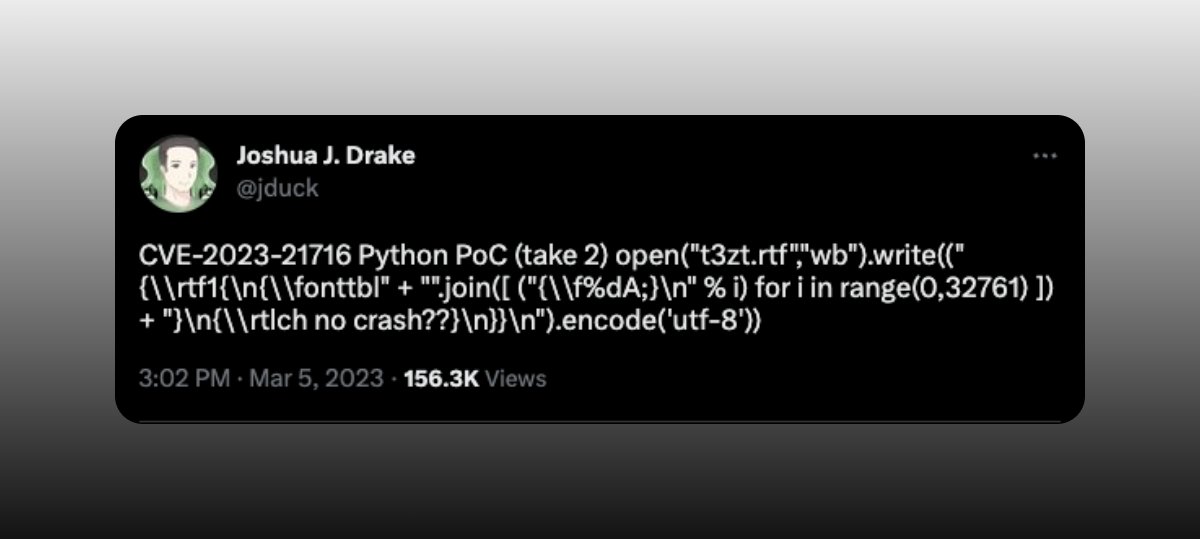
Wallet Guard on X: ⚠️ SECURITY ALERT 🗒️ 0-CLICK Microsoft Word RCE exploit Microsoft identifies this exploit as critical. It is important to avoid .rtf files at all costs! / X

How to Exploit WebDAV on a Server & Get a Shell « Null Byte :: WonderHowTo

After exploit when try to login: Cannot open file for writing log · Issue #12 · XiphosResearch/exploits · GitHub
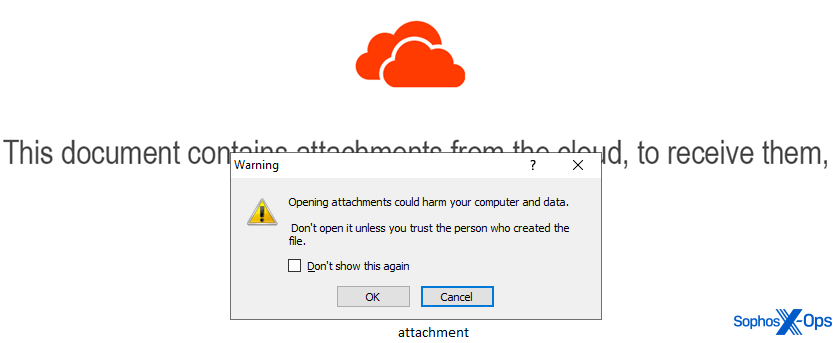
Qakbot mechanizes distribution of malicious OneNote notebooks – Sophos News

Picasso updated to v3 open beta 4 with smaller file size & several more bug fixes

Flaw In Library Leaves Gnome Users Open to Remote Code Exploit

Hack the Box Write-Up: DEVEL (Without Metasploit)
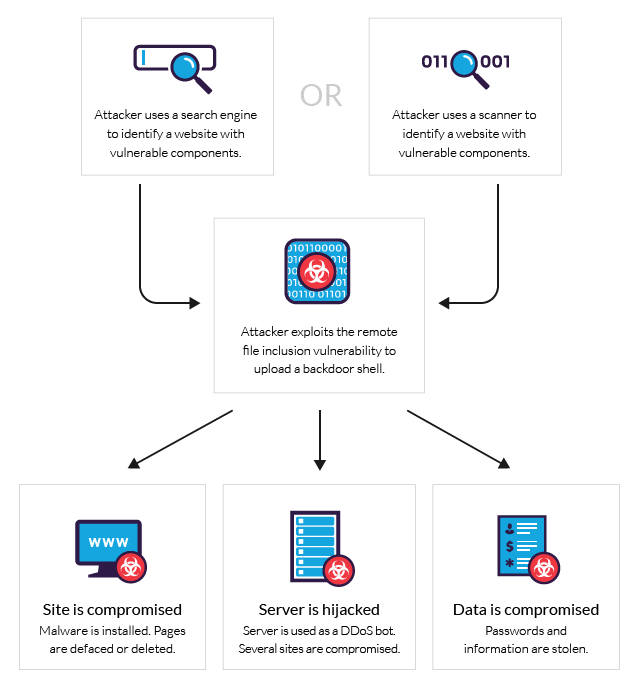
What is RFI, Remote File Inclusion Example & Mitigation Methods
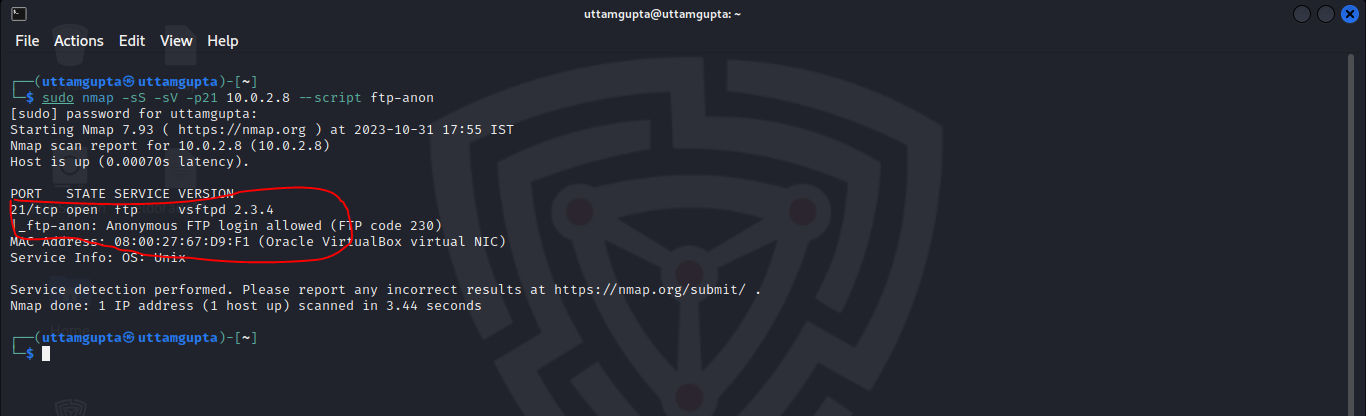
Port 21 Exploit 🔍🔎. HELLO there, I am back again with an…, by Uttam Gupta, Oct, 2023
de
por adulto (o preço varia de acordo com o tamanho do grupo)