Indirect Command Execution – Penetration Testing Lab
Por um escritor misterioso
Descrição
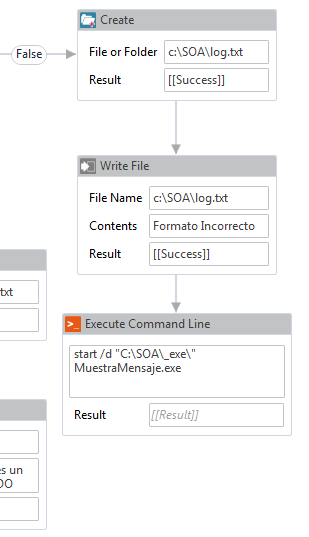
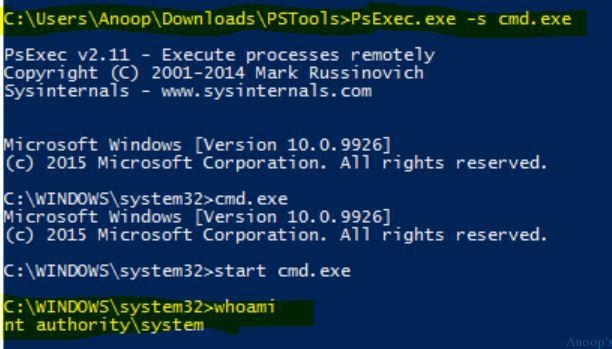
The windows ecosystem provides multiple binaries that could be used by adversaries to execute arbitrary commands that will evade detection especially in environments that are monitoring binaries such as "cmd.exe". In certain occasions the techniques described below could be used to bypass application whitelisting products if rules are not configured properly (whitelist by path or…

Indirect Command Execution – Penetration Testing Lab
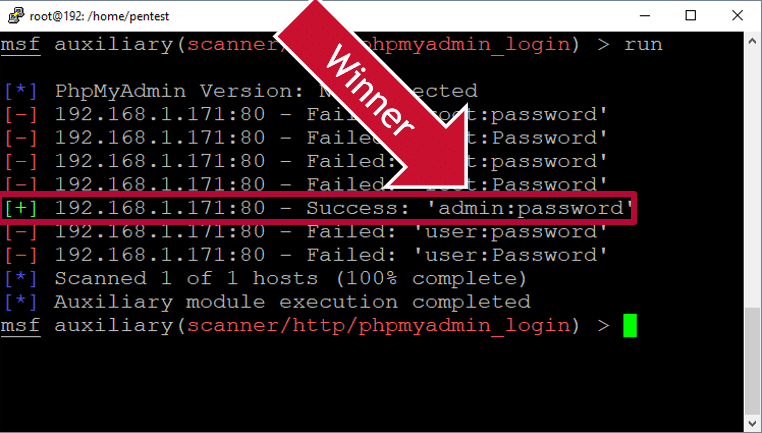
Linux Hacking Case Studies Part 3: phpMyAdmin
Boosting cybersecurity: Siemens launches new all-in-one security testing suite for industrial networks, Press, Company

Indirect Command Execution

Windows Print Spooler RCE Vulnerabilities (CVE-2021-1675/CVE-2021-34527) Mitigation Guide - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Quick — HackTheBox. Penetration Testing Labs, by y4th0ts
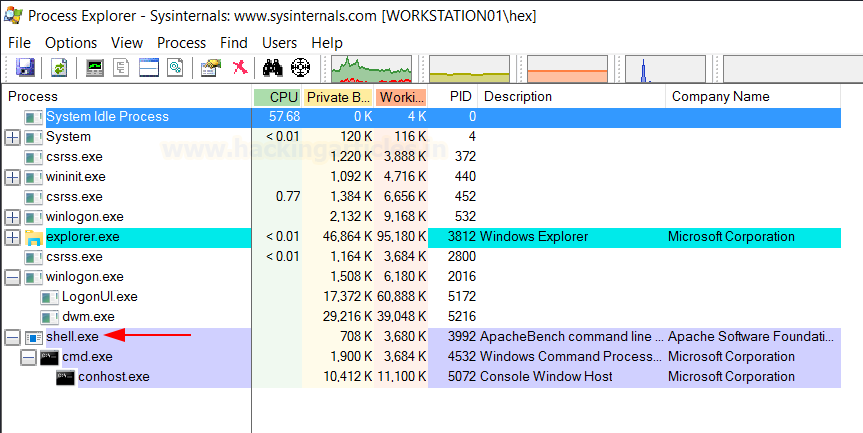
Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles
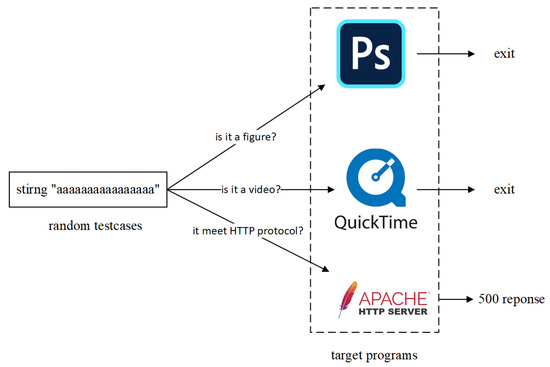
Electronics, Free Full-Text
Securing LLM Systems Against Prompt Injection

Indirect Command Execution – Penetration Testing Lab

Indirect Command Execution – Penetration Testing Lab

PentesterLab: Learn Web App Pentesting!
de
por adulto (o preço varia de acordo com o tamanho do grupo)