Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo
Por um escritor misterioso
Descrição
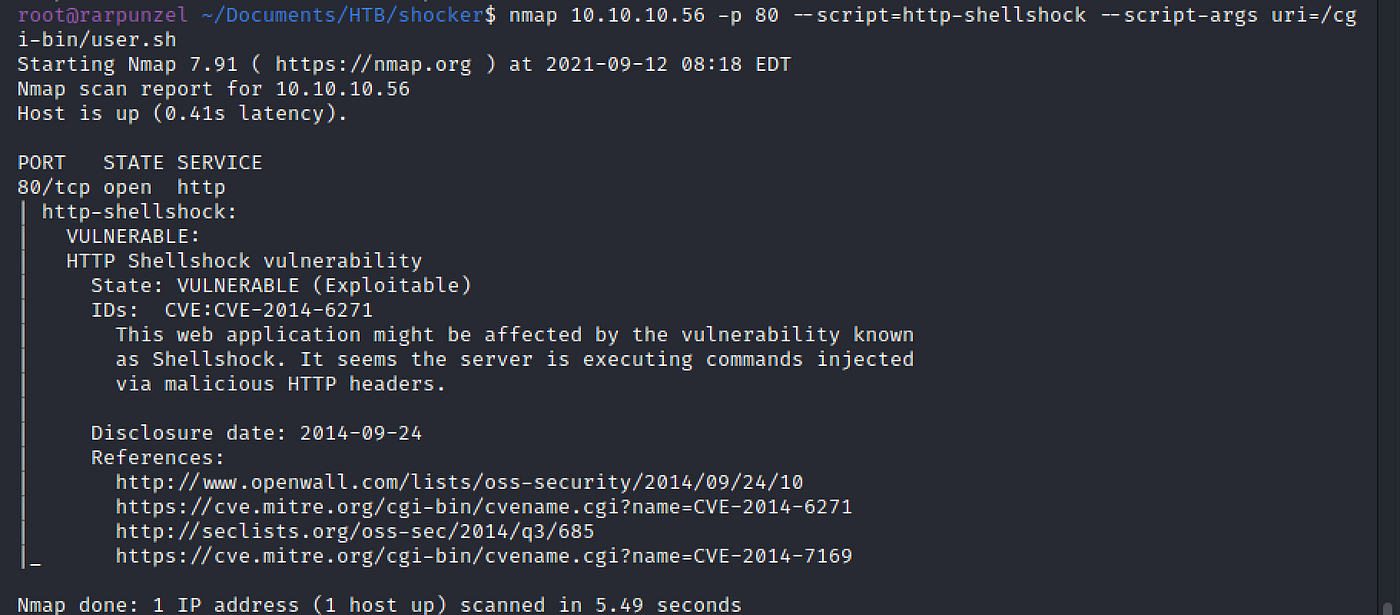
Hack The Box Shocker Write-Up (Without Metasploit), by rarpunzel

Network Hacker Stickers for Sale
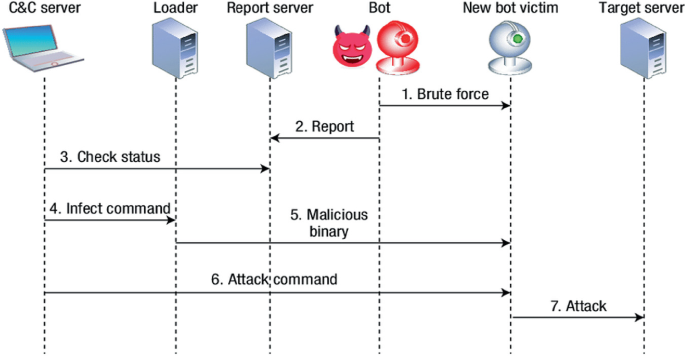
Determining Vulnerabilities of Pervasive IoT Devices and Their Geographic Distribution

Android for Hackers: How to Scan Websites for Vulnerabilities Using an Android Phone Without Root « Null Byte :: WonderHowTo
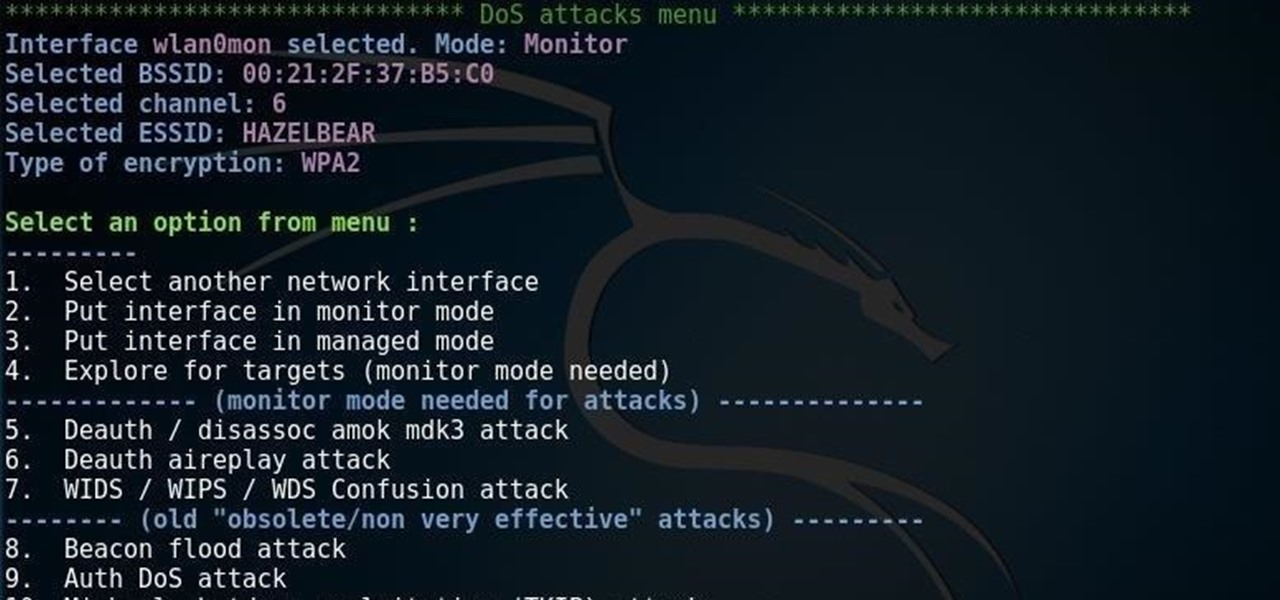
Should Null Byte Start a YT Playlist for Better Understanding of Hacking Processes?? « Null Byte :: WonderHowTo

CEHv9 11 - Hacking Webservers - Stoner - April 2017, PDF, Internet Information Services

Hack Like a Pro « Null Byte :: WonderHowTo

The ShellShock Vulnerability Explained
GitHub - hacker-insider/Hacking

technical] Pen-testing resources, by Dragon Security

The hackers manual 2015 revised edition by Gerson Villa Gonzalez - Issuu

ECCouncil 312-50 Exam Actual Questions 14 PR 19 v8, PDF, Firewall (Computing)
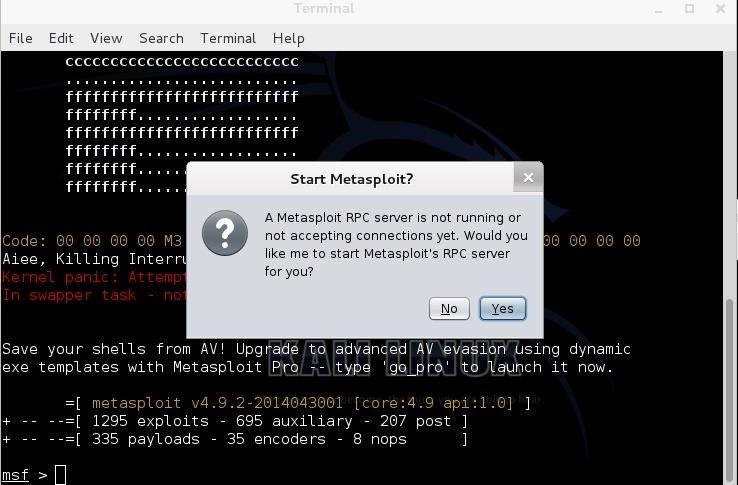
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 1 (Primer & Overview) « Null Byte :: WonderHowTo
de
por adulto (o preço varia de acordo com o tamanho do grupo)