SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Descrição
As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.
AV/EDR Evasion, Malware Development P-3
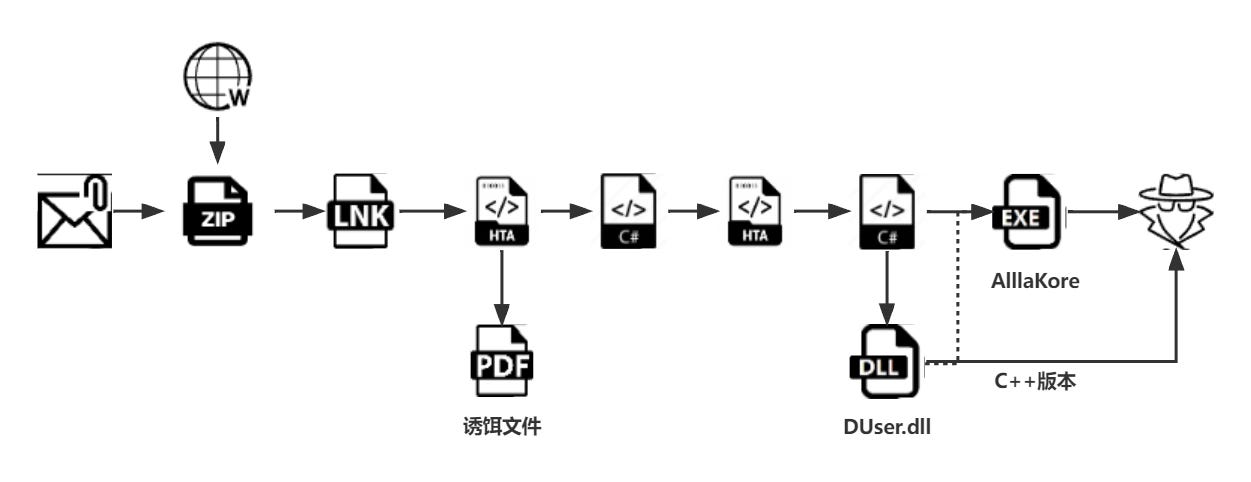
Chinese hackers use new custom backdoor to evade detection

1-15 March 2023 Cyber Attacks Timeline – HACKMAGEDDON

Simjacker

Evading AV with Veil-Evasion

SILKLOADER: How Hackers Evade Detection

How Hackers Evade Detection

SILKLOADER: How Hackers Evade Detection

Malware - Wikipedia

SILKLOADER: How Hackers Evade Detection

Spyder Loader: Malware Seen in Recent Campaign Targeting Organizations in Hong Kong
Bluepurple Pulse: week ending March 26th - by Ollie

Evading AV Software « Null Byte :: WonderHowTo

How Hackers Are “Blending In” to Evade Detection

Chinese Hackers Use New Cryptojacking Tactics to Evade Detection
de
por adulto (o preço varia de acordo com o tamanho do grupo)