Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null
Por um escritor misterioso
Descrição
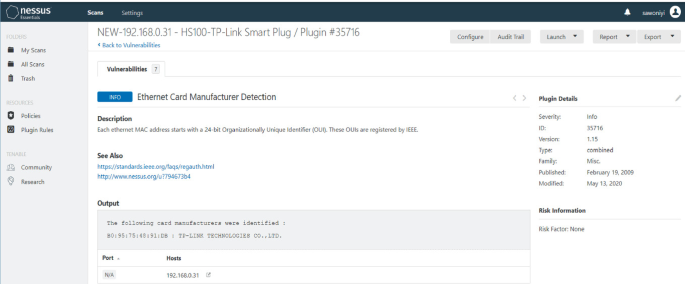
Determining Vulnerabilities of Pervasive IoT Devices and Their Geographic Distribution

The hackers manual 2015 revised edition by Gerson Villa Gonzalez - Issuu

Hacking Tizen : The OS of Everything - Nullcon Goa 2015

Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo
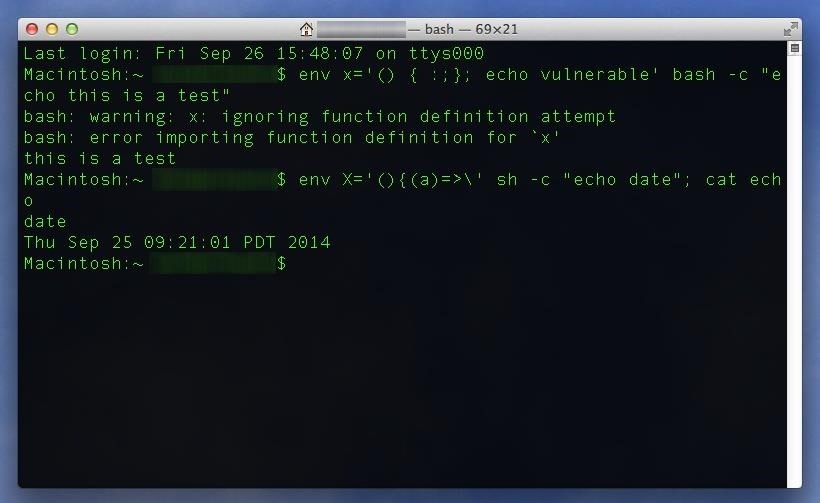
Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X « Mac OS Tips :: Gadget Hacks
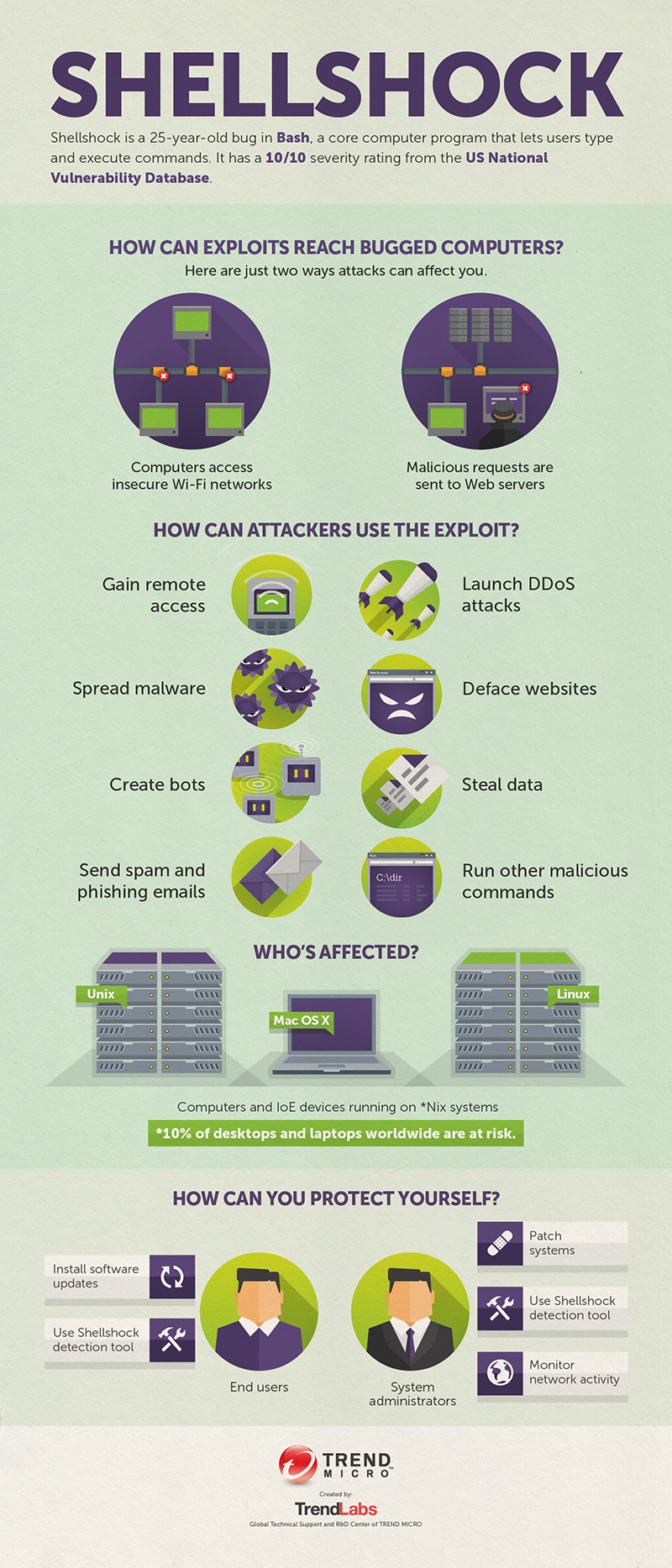
About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Security News

Tech Tools For Activism - Pentesting - Penetration Testing - Hacking - #OpNewBlood, PDF, Command Line Interface

Keep Calm and Hack The Box - Shocker

Message Authentication and Provenance Verification for Industrial Control Systems

Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X « Mac OS Tips :: Gadget Hacks

All labs Web Security Academy

BSidesJXN 2017 - Improving Vulnerability Management

Processing tweets for cybersecurity threat awareness - ScienceDirect
de
por adulto (o preço varia de acordo com o tamanho do grupo)
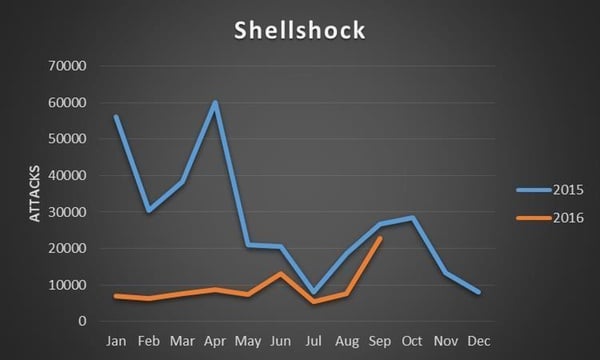


.jpg&h=420&w=748&c=0&s=0)



