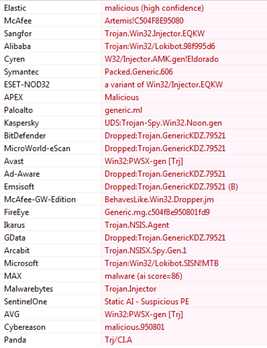
contagio: Trojan.Hydraq detection and naming
Por um escritor misterioso
Descrição

The Works of Vicesimus Knox, vol. 5

Ethical hacking for IoT: Security issues, challenges, solutions and recommendations - ScienceDirect

Surveillance Capitalism or Democracy? The Death Match of Institutional Orders and the Politics of Knowledge in Our Information Civilization - Shoshana Zuboff, 2022

Type of Hardware Trojan Detection Techniques The hardware Trojan

Mal-Detect: An intelligent visualization approach for malware detection - ScienceDirect

Malware Dr. Tyler Bletsch - ppt download

Trojan Horse: The Hidden Danger of Banker Trojans - FasterCapital

Mal-Detect: An intelligent visualization approach for malware detection - ScienceDirect
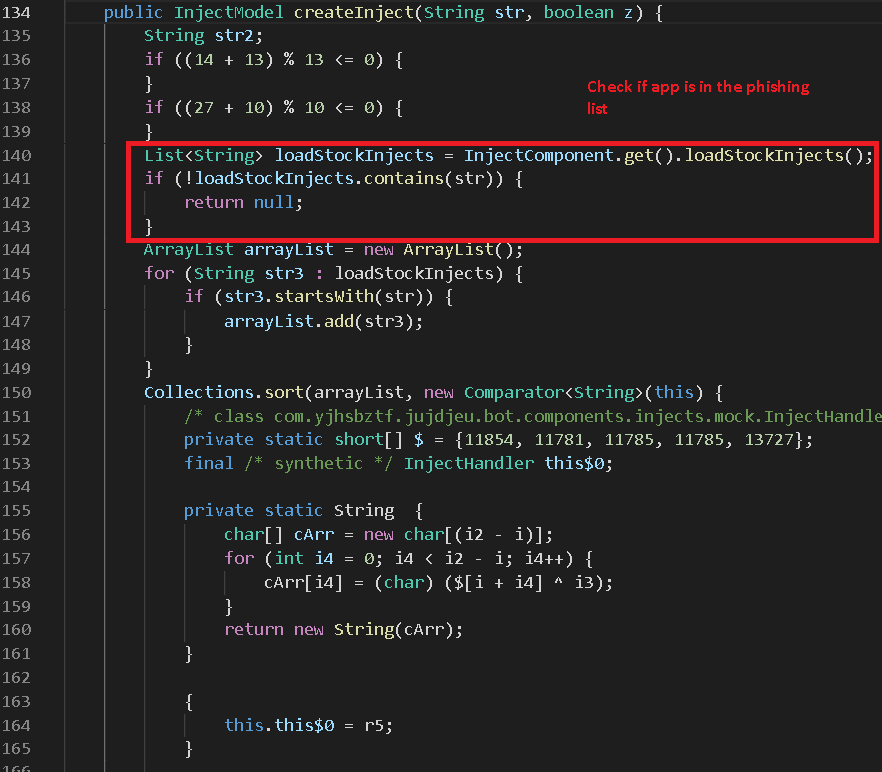
Avira Labs Research Reveals Hydra Banking Trojan 2.0 targeting a wider network of German and Austrian banks

Malware Dr. Tyler Bletsch - ppt download
contagio: February 2010

What Is a Remote Access Trojan? Remove and Prevent RATs
de
por adulto (o preço varia de acordo com o tamanho do grupo)