How ransomware attackers evade your organization's security
Por um escritor misterioso
Descrição
How ransomware operators avoid your security solutions and what you can do to protect your network against post-compromise ransomware attacks.

Top 7 Ransomware Attack Vectors & How to Avoid Becoming a Victim

How to protect your organization from ransomware attacks

RH-ISAC, Preventing Ransomware Attacks in a Hybrid Cloud

How To Prevent Ransomware Attacks (Expert Guide)
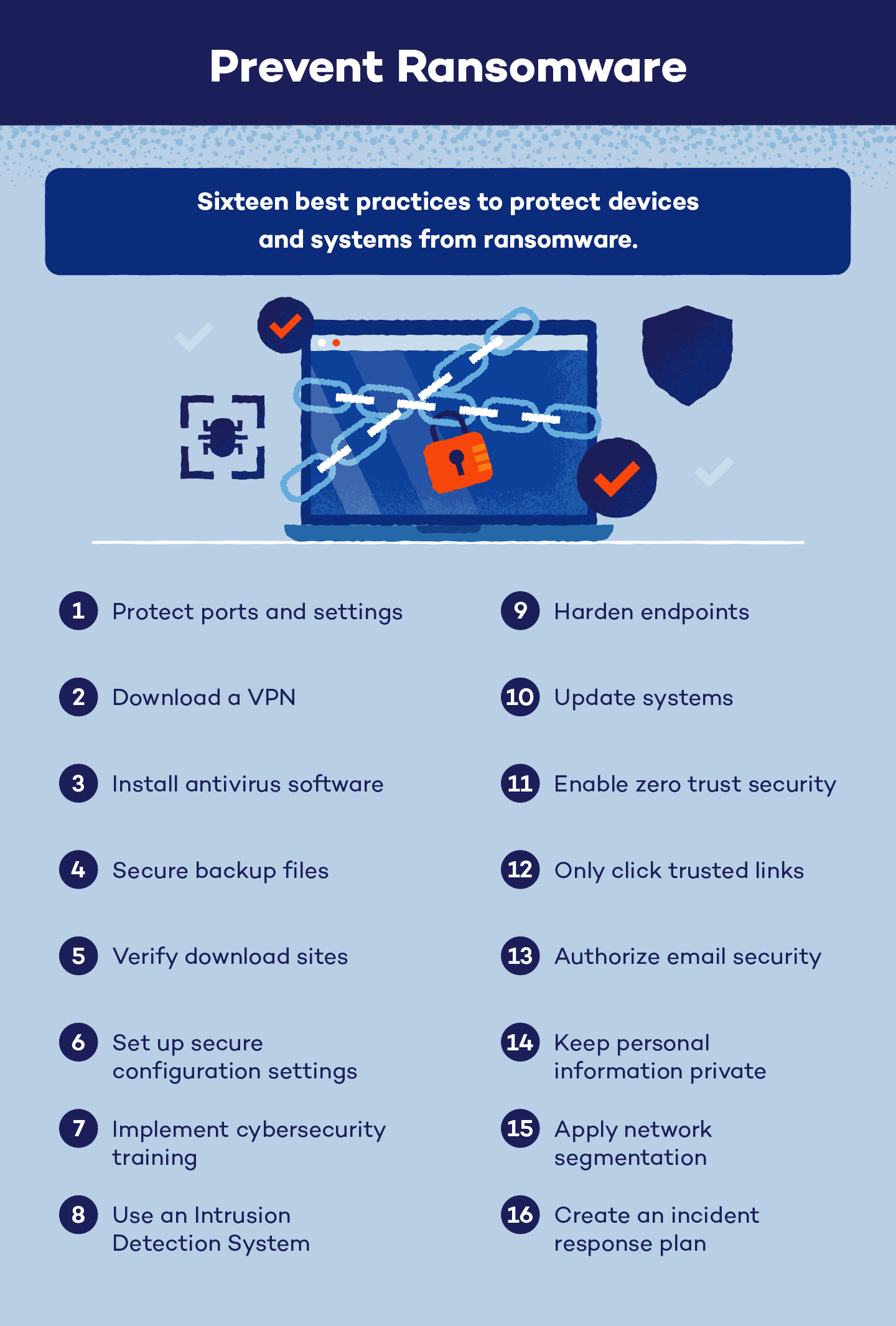
Prevent Ransomware with 16 Best Practices - Panda Security

What's New in Ransomware & How to Avoid an Attack - The Wursta Corporation
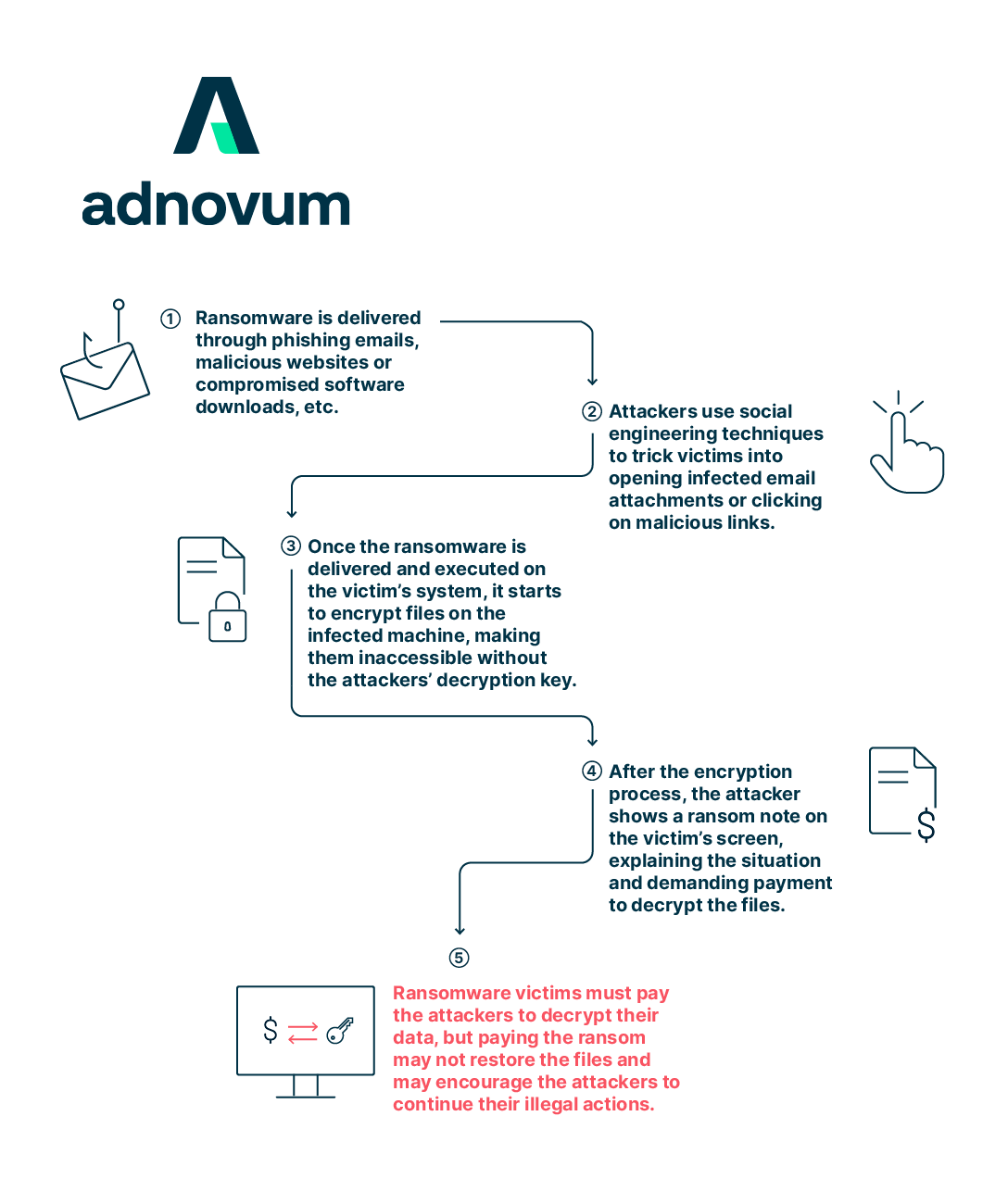
Guide to Protecting Your Business Against Ransomware Attacks
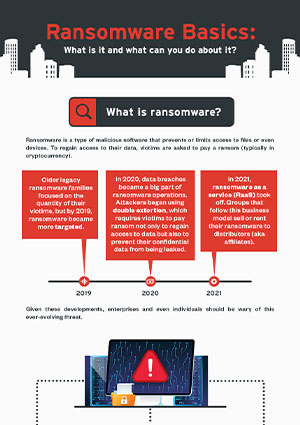
Ransomware - Definition

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

What to Do If a Ransomware Attacks Your Computer

Ransomware Attacks

9 stages of ransomware: How AI responds at every stage
de
por adulto (o preço varia de acordo com o tamanho do grupo)


:strip_icc()/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/F/Z/AAVPy7QcKzQCbDu6AjLg/kindle-paperwhite-02.jpg)