Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Descrição
Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

Malware: Types, Examples, and How Modern Anti-Malware Works

How can an attacker execute malware through a script? 2022

10 Malware Examples and 6 World Famous Attacks

Exploring Prompt Injection Attacks

Machine learning and blockchain technologies for cybersecurity in

Three flaws allow attackers to bypass UEFI Secure Boot feature

Attacking Artificial Intelligence: AI's Security Vulnerability and

Cybersecurity's Biggest Mistakes of 2022 - SentinelOne

Outsmarting Generative-AI Attacks: The Power of Automated Moving
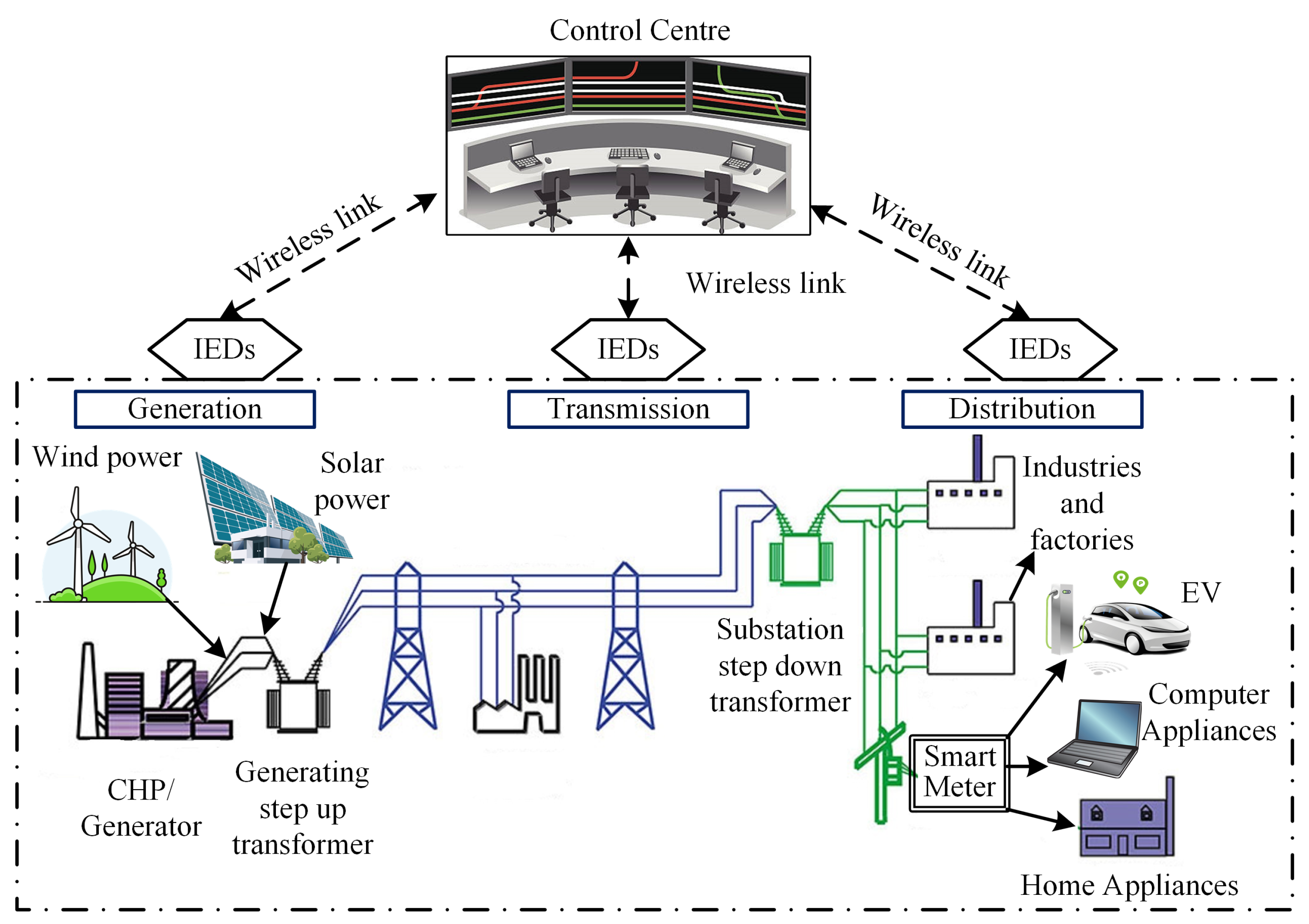
Electronics, Free Full-Text

Types of Cyber Attacks You Should Be Aware of in 2024

Antivirus & Malware Evasion Techniques

Living-Off-the-Land (LOTL) Attacks: Everything You Need to Know

Metador APT hackers target telecommunications, ISPs, universities
de
por adulto (o preço varia de acordo com o tamanho do grupo)