Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Descrição

Vulnerability Scanning in your CI/CD Pipeline - Part Two
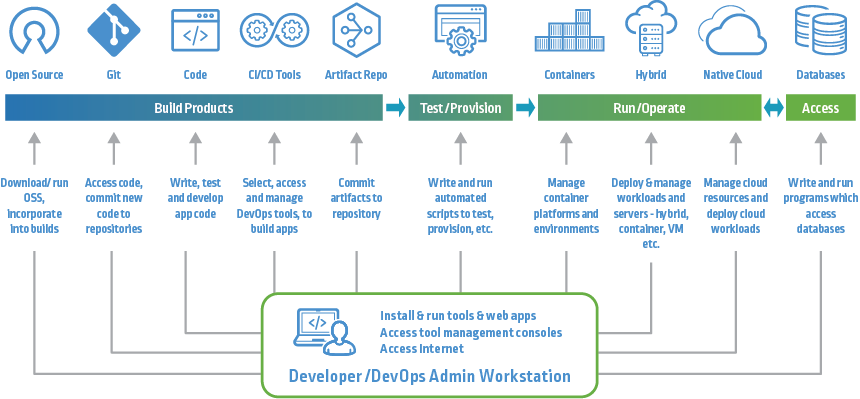
What is CI CD Pipeline? - CI/CD Pipeline Definition

Implement DevSecOps to Secure Your CI/CD Pipeline

Getting Started With CI/CD Pipeline Security - DZone Refcardz
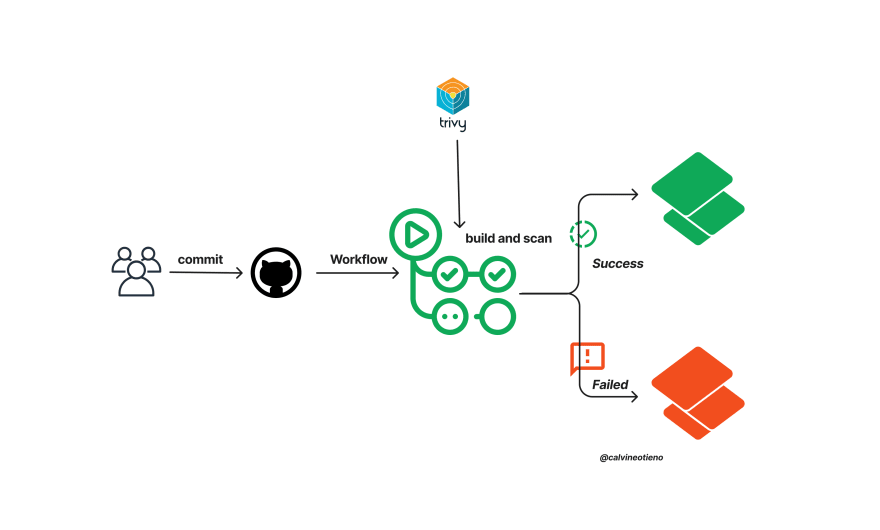
Improving your CI/CD Pipeline: Helm Charts Security Scanning with Trivy and GitHub Actions - DEV Community

Vulnerability Scanning in your CI/CD Pipeline - Part Two
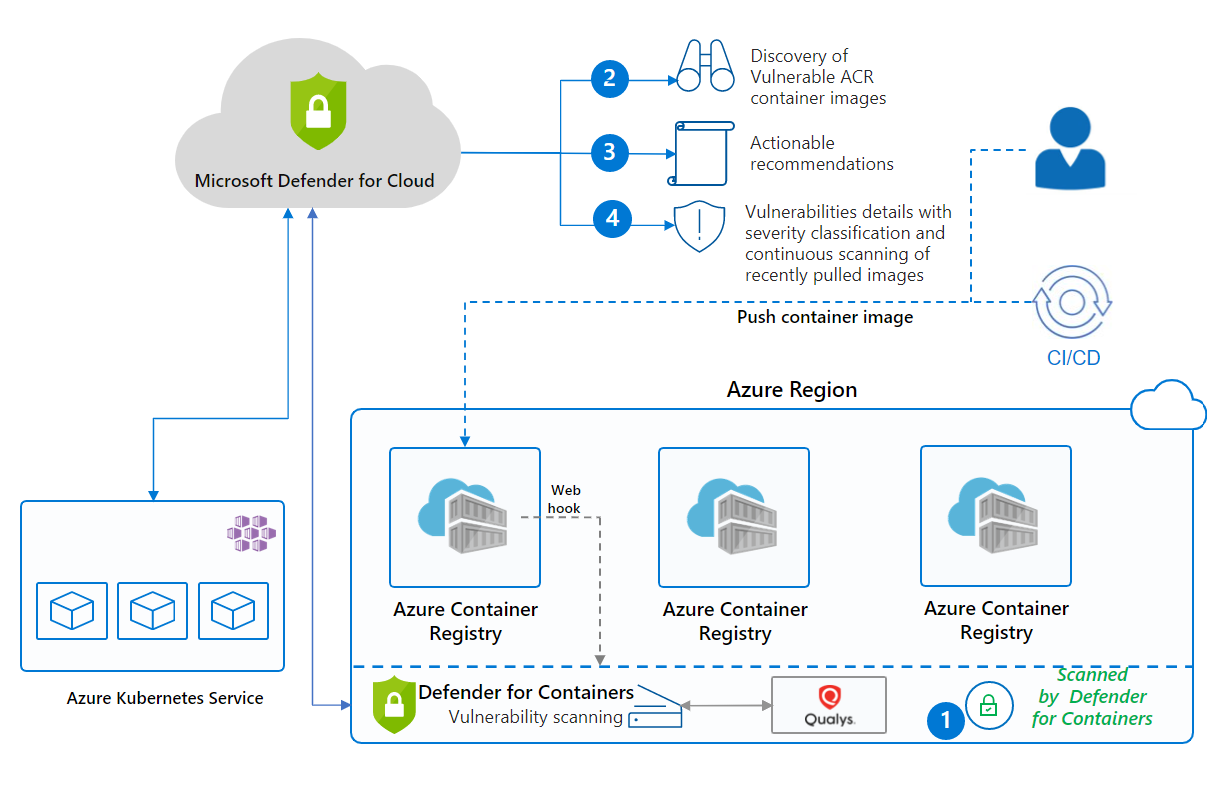
Enhance your CI/CD deployment by using Vulnerability Assessments from Microsoft Defender for ACR - Microsoft Community Hub
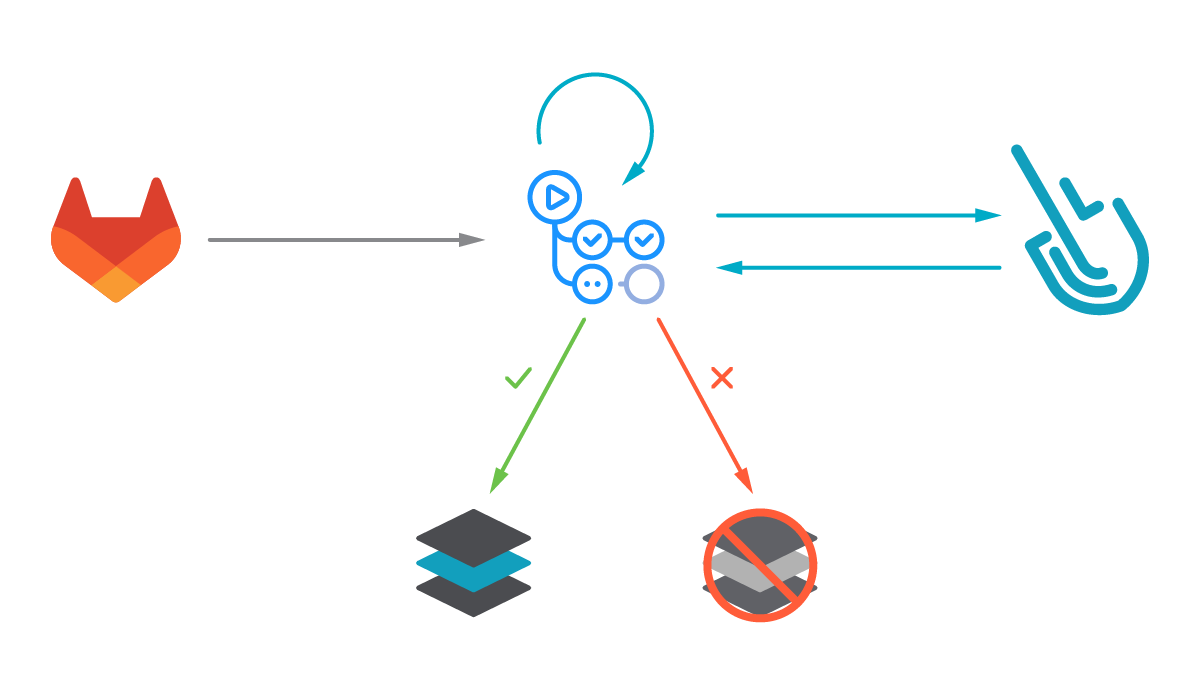
Image scanning for GitLab CI/CD – Sysdig
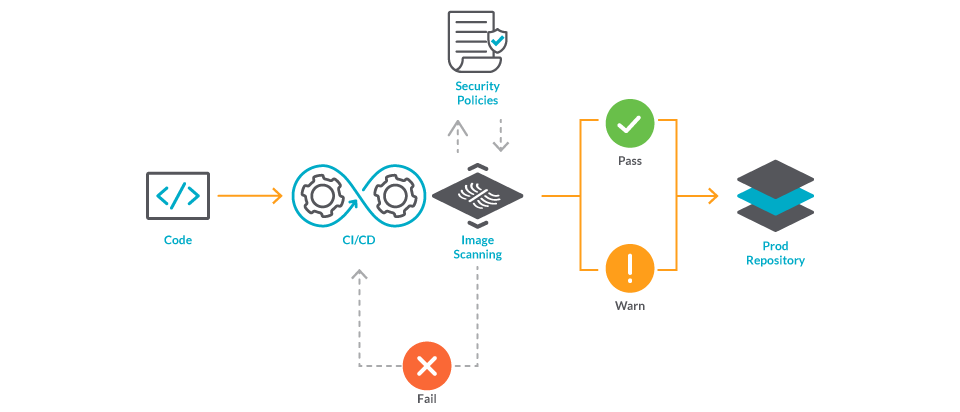
Top vulnerability assessment and management best practices – Sysdig

CI/CD Security Best Practices
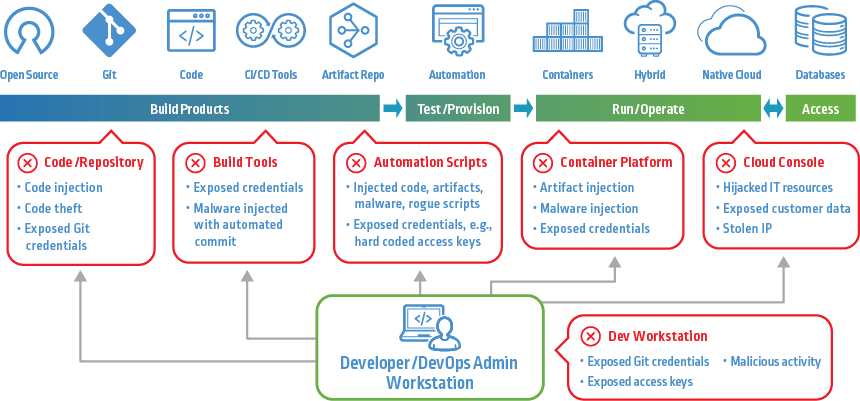
What is CI CD Pipeline? - CI/CD Pipeline Definition

Scan for vulnerabilities early to shift security left in CI/CD
de
por adulto (o preço varia de acordo com o tamanho do grupo)