Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Descrição
Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

One Click Hijack: Vulnerability in TikTok Android App?
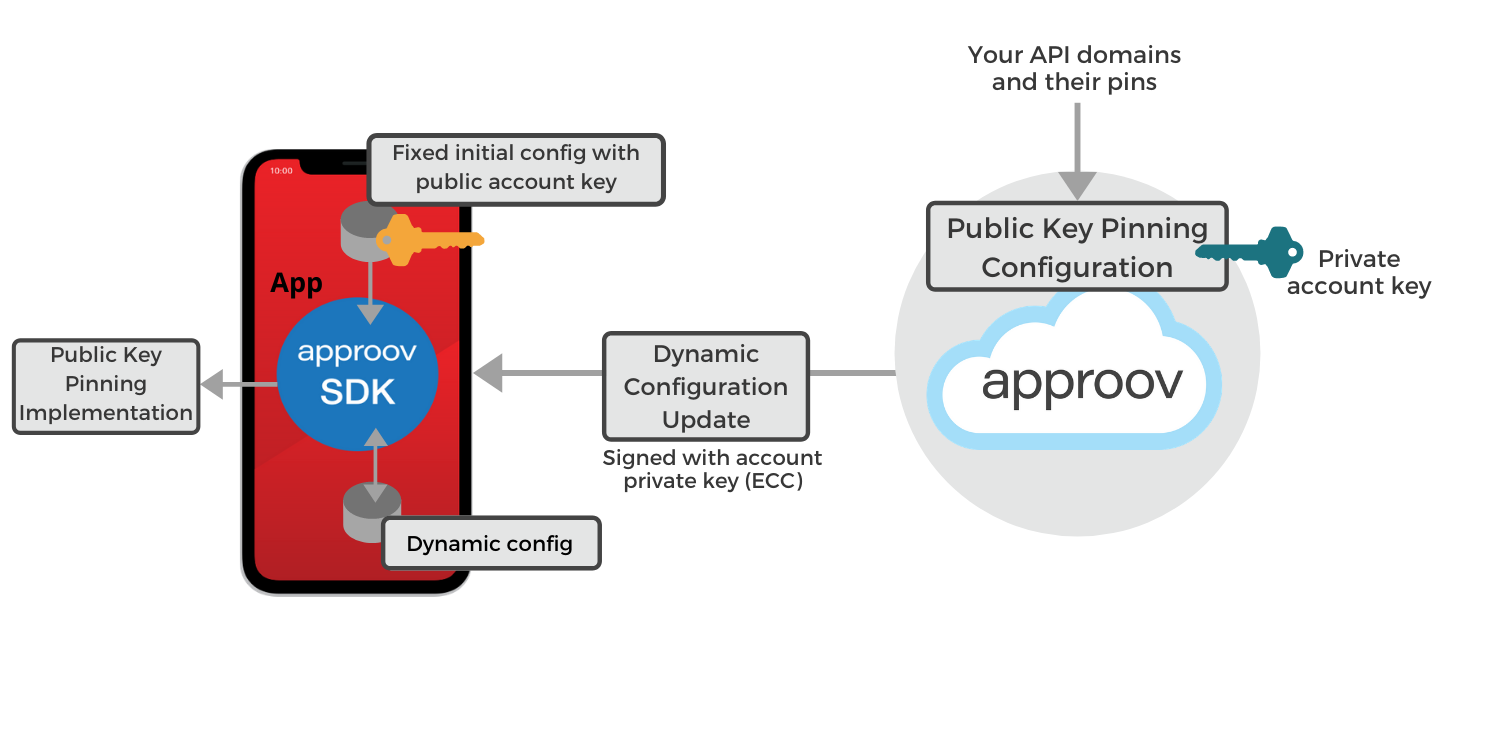
How to Protect Against Certificate Pinning Bypassing

Attackers uses repackaging to publish forged applications on

Prevent Reverse Engineering (RE) of your Android application

9 New Fake Apps on the Play Store Which Can Hijack SMS

This is how malicious Android apps avoid Google's security vetting

What Is Rootkit?
%20-%20refresh/img_03.png?width=350&name=img_03.png)
Android App Permissions: Which to Allow and Avoid

Android Applications Pentesting - HackTricks

Google Play threat market: overview of dark web offers
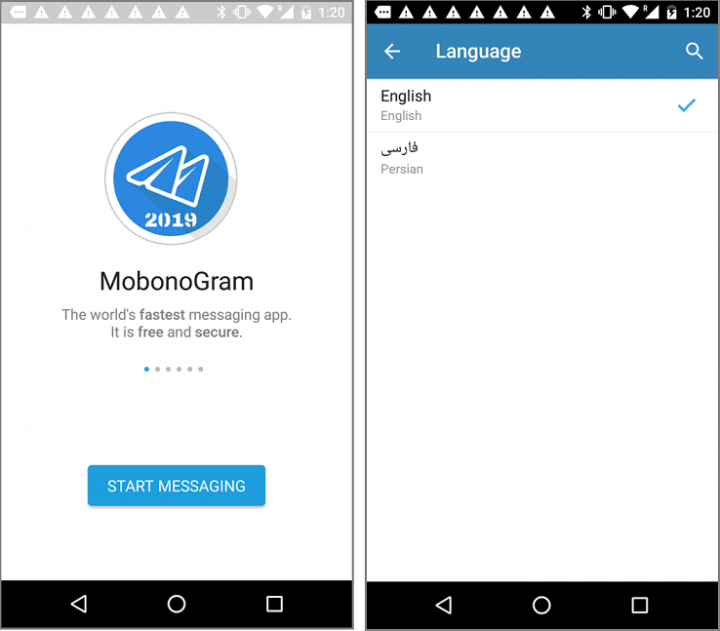
Unofficial Telegram App Secretly Loads Infinite Malicious Sites
de
por adulto (o preço varia de acordo com o tamanho do grupo)