How hackers use idle scans in port scan attacks
Por um escritor misterioso
Descrição
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

NMap 101: Fun With Firewalls! HakTip 102
Ethical Hacking: Scanning Networks (2016) Online Class

Nmap cheat sheet: From discovery to exploits, part 2: Advance port scanning with Nmap and custom idle scan

Port Scanning Tutorial for Hackers - Basics
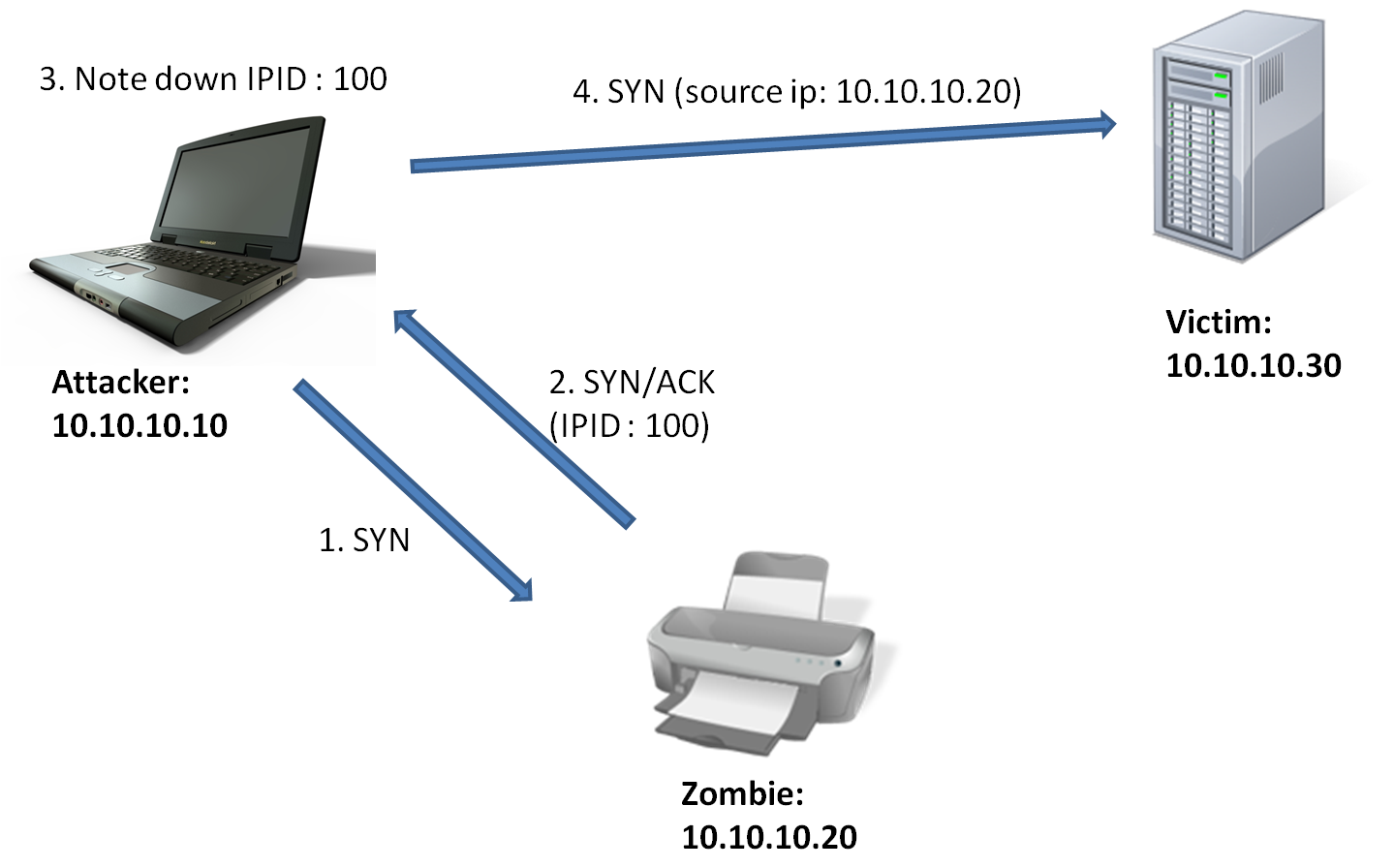
Vipul Chaskar's Blog: How does idle scan work?
What is Port Scanner? Scanning Ports - ManageEngine OpUtils
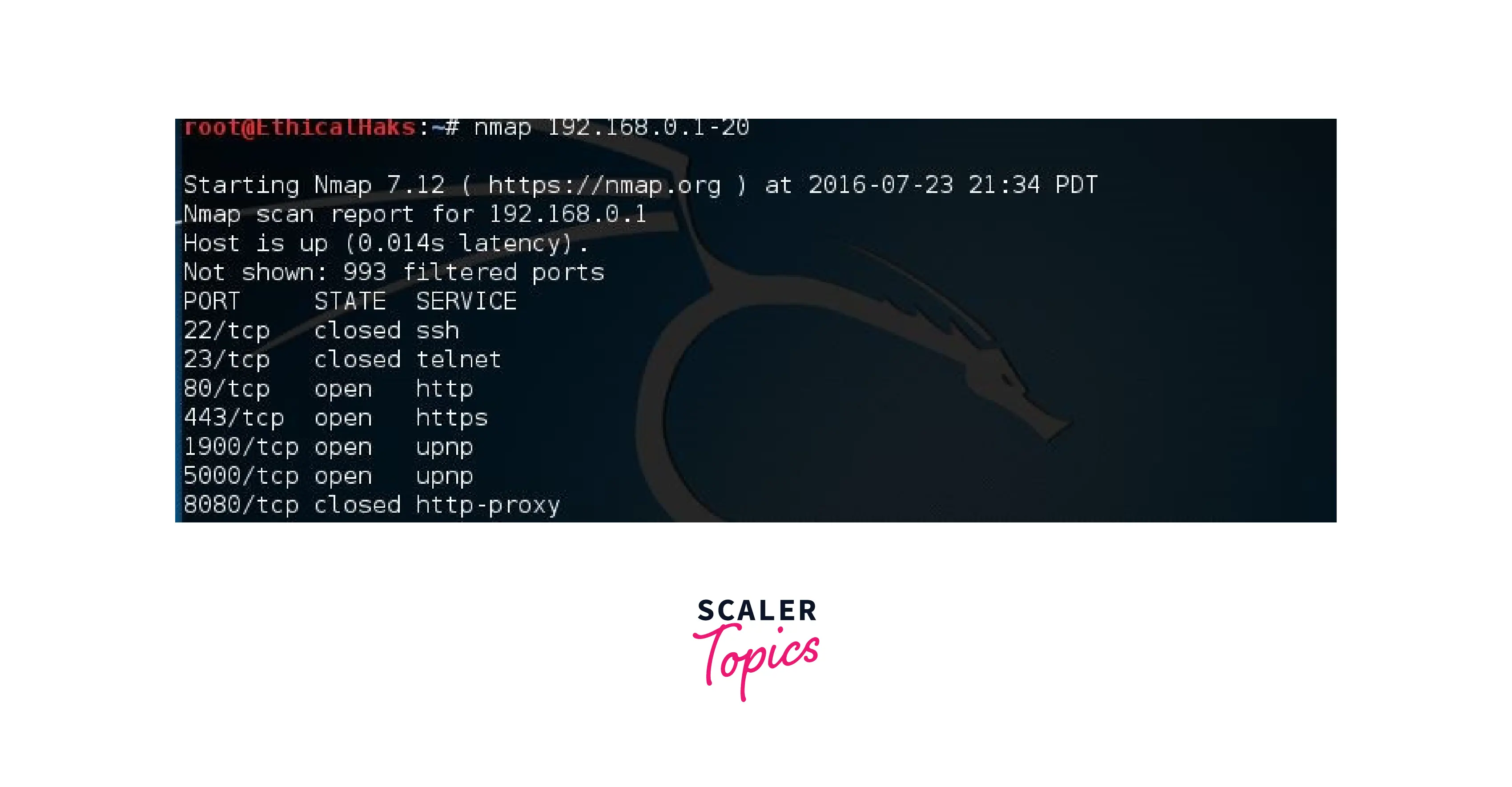
Introduction to Network Auditing with Nmap - Scaler Topics
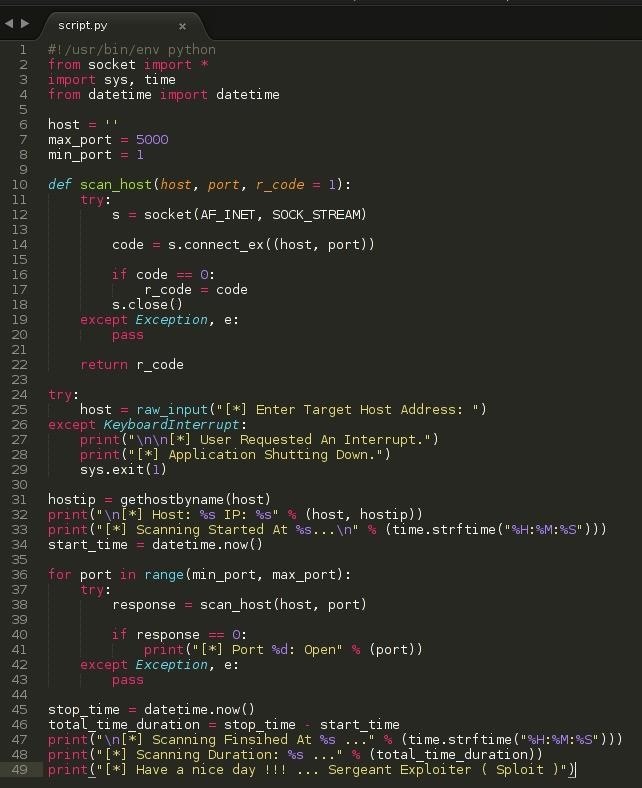
SPLOIT: How to Make a Python Port Scanner « Null Byte :: WonderHowTo

Performing an Idle Zombie Scan Nmap

PDF) Surveying Port Scans and Their Detection Methodologies
de
por adulto (o preço varia de acordo com o tamanho do grupo)